
When it comes to conducting transactions, the possibility of fraud is always a risk that cannot be overlooked. In person, an individual may present forged or altered documents attesting to an identity that is not his or her own.
An individual could similarly misrepresent his or her identity online by using someone else's credentials without their permission. This is where online user authentication can attest to a person's or entity's identity and ensure the transaction's validity.
What is Authentication?
The term authentication refers to an electronic process that allows a natural or legal person to be electronically identified. Furthermore, authentication can be used to confirm the origin and integrity of data in electronic form, such as the issuance of a digital certificate to verify the authenticity of a website. The overall goal of authentication is to reduce the possibility of fraud, particularly when an individual purposefully misrepresents their identity or uses another person's credentials without authorization.
The terms digital authentication or electronic authentication (e-authentication) synonymously refer to the process where the confidence in user identities is established and presented electronically to an information system.
The digital authentication process presents a technical challenge due to the necessity of authenticating individual people or entities remotely over a network.
Its level of security depends on the applied type of authentication, the authentication factors used, as well as the process of authentication applied.
This article describes these relevant dimensions of security in the following sections.
Authentication Factors
When authenticating an online user, three types of factors can be used to ensure that the user is who he or she claims to be. These are the factor categories:
- Knowledge factors – these would include a user's password, passphrase, personal identification number (pin), or a challenge response in which the user would be required to answer a pre-selected security question.
- Ownership factors –These would include items in the user's possession, such as a bank card, a hardware or software one-time password (OTP) token, or a cell phone.
- Inherence factors – biometric identifiers such as facial, fingerprint, or retinal pattern recognition, as well as other personal trait identifiers, are examples of these factors.
Types of Authentication
The following classification lists the most commonly used types of online user authentication, sorted by increasing levels of security:
- Single-factor authentication - only one component out of one of the 3 factor categories is used to authenticate a person’s identity. Experience shows that one single factor does not provide sufficient protection against malicious intrusion and misuse. Therefore, as soon as financially or personally relevant transactions are involved, a higher level of security is preferable.
- Two-factor authentication – often referred to as 2FA, the user’s identity is confirmed by using a combination of two independent components from two different factor categories. For example, where a user has logged on to their online bank account, with their username and password, and wishes to complete an online transaction, he or she would need to enter an authentication factor in addition to the knowledge factor (username and password) that was used to log on. The additional factor must also be from a different factor category than the username and password. An online banking user would typically use an authentication mechanism from the ownership category such as an OTP device or mobile phone to receive an OTP in a text message. OTPs are dynamic passwords which can only be used once and thereby provide a strong level of protection against a range of attacks.
- Multi-factor authentication is similar to 2FA, but it can combine more than 2 authentication factors for enhanced security, whereas 2FA only uses two different factors.
- Strong authentication – this type is often used as synonym for multi-factor authentication or 2FA. However, unlike multi-factor authentication and 2FA, strong authentication mandatorily requires non replicable factors or the use of digital certificates to provide a higher level of authentication for users. If those criteria are fulfilled, multi-factor authentication and 2FA are able to provide strong authentication.
The European Central Bank (ECB) defines strong customer authentication as “a procedure based on two or more of the three authentication factors, 1. Knowledge, 2. Ownership, and 3. Inherence. According to the ECB definition, the individual elements that are chosen for strong authentication factors must be mutually independent and at least one must be “non-reusable and non-replicable (except for inherence), and not capable of being surreptitiously stolen via the internet.” What does that mean? Independence is relatively easy to grasp - if one component is related to the other, hacking one means all components are tampered with. Non-replicability implies the aspect of time or usage. Used once it cannot be used again. An example is a one-time-password which is only valid during a short period of time (e.g., 30 seconds).
In the United States, the National Information Assurance (IA) Glossary produced by the Committee on National Security Systems defines strong authentication similarly, requiring “multiple factors for authentication and advanced technology, such as dynamic passwords or digital certificates to verify an entity’s identity.” Dynamic passwords include the aspect of time. In deviation to the ECB definition, the IA also accepts cryptographic means such as a public key certificates to co-authenticate a user.
Enrolment and Authentication Process
The American National Institute of Standards and Technology (NIST) has outlined a quite generic digital authentication model, which can be used as a basic explanation model for the authentication process, regardless of the geographical region or area of jurisdiction.
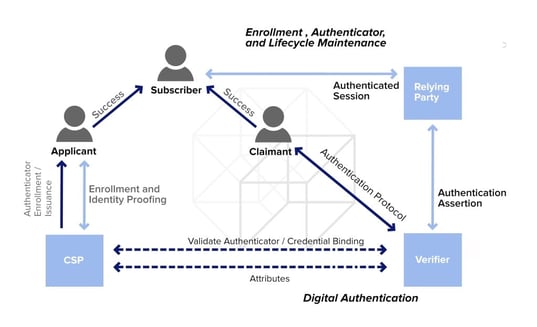
Source: NIST Authentication Guideline (2016)
In the NIST model, an individual (applicant) applies to a credential service provider (CSP) and thus initiates the enrolment process. Once the CSP has successfully proven the applicant’s identity, he or she becomes a “subscriber”, and an authenticator (e.g., token) as well as a corresponding credential, such as a username, are established between the CSP and the applicant (now owning the the role of the subscriber).
The CSP has the task of maintaining the credential including its status and all enrolment data over the whole lifetime of the credential. The subscriber needs to maintain the authenticator(s). This first part of the NIST reference model is applied in any enrollment process, where subsequent authentication is required, e.g., when a bank account is created or when a person signs up in an e-government process.
Once the applicant has become a “subscriber”, he or she can perform online transactions within an authenticated session, conducted with a relying party. In such a transaction, the person holds the role of a claimant, proving to a verifier the possession of one or more authenticators. Verifier and relying party might be the same or alternatively two independent entities. If verifier and relying party are separate, the verifier has to provide assertion about the subscriber to the relying party. Subsequent to this this assertion, the relying party may then initiate the transaction process.
In the following, a typical payment sequence illustrates this reference process:
The account owner (“subscriber) wants to initiate a transaction. He or she first needs to prove through one or more authenticators that he or she, who claims to be the account owner (“claimant”) actually is the person he claims to be (“subscriber). The validation is done by a “verifier” who verifies the authenticators at the “credential service provider” and after validation gives authentication assertion to the transaction department of the bank (relying party). In many banks the entities “verifier” and “credential service provider” may well be entities within the the bank.
E-government processes are conducted in a similar way (e.g. the application for a passport). But in many cases, the “credential service providers” are external entities.
As already described in the section on types of authentication, this generic reference process can be implemented depending on the requirements and areas of jurisdiction.
Conclusion
The burden of fraudulent transactions falls upon individuals, businesses and financial institutions with losses that result in costs passed down to consumers along with costs related to identity theft. Authentication is one means to protect online transactions, along with their sender or recipient from falling victim to fraud.
Other concepts such as digital signing can also leverage (strong) authentication to achieve better security, data integrity and non-repudiation for digital transactions.
References and Further Reading
- Selected articles on Authentication (2014-16), by Heather Walker, Luis Balbas, Guillaume Forget,and Dawn M. Turner
- Selected articles on Electronic Signing and Digital Signatures (2014-16), by Ashiq JA, Guillaume Forget, Peter Landrock, Torben Pedersen, Dawn M. Turner and Tricia Wittig
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
- Recommendations for the Security of Internet Payments (Final Version) (2013), by the European Central Bank
- Draft NIST Special Publication 800-63-3: Digital Authentication Guideline (2016), by the National Institute of Standards and Technology, USA.
- NIST Special Publication 800-63-2: Electronic Authentication Guideline (2013), by the National Institute of Standards and Technology, USA.
- Security Controls Related to Internet Banking Services (2016), Hong Kong Monetary Authority
Image: StartupStockPhotos.com (CC0 Licence), Artwork by VentureSkies
