Demystifying Mobile Application Hardening: Techniques and Best Practices
This blog runs through Mobile App Hardening and the techniques and best practices for implementing it.
Mobile devices handle huge amounts of increasingly sensitive data, which means apps delivering banking, mobile wallet, healthcare, ID services, and more cannot afford to be broken.
In over ten years of providing a secure mobile core software development kit (SDK), we have protected over 100 million+ apps, with no recorded incidents. It’s no wonder that frustrated hackers have described our protection as ‘watertight’!
We're cryptographic experts constantly studying attacks of a quantum nature, helping you manage secrets.
We don’t just provide a wrap-around shield, or an add-on. Our mobile application protection gives you true in-app security based on multiple interlocking layers that help you comply with regulations and keep data secure
/Mobile%20Application%20Security/GRAFX.png?width=300&height=256&name=GRAFX.png)
It also exposes a larger attack service, which requires a very particular skillset to better manage increased risk and protect against financial devastation or reputational disaster.
Our unrivalled experts craft mobile protection solutions that deliver the highest levels of security by design. We don’t just provide a shield, or an add-on; our mobile protection gives you true in-app security.
We provide the highest levels of security. Our solutions constantly undergo extensive penetration (PEN) testing to achieve certification and ensure we:
This provides you with a fast-track to compliance with regulations including:
Developers can focus on app’s user experience and business logic and we take care of the security. Exposure areas are consequently limited making life easier for security architects and compliance officers.
/Mobile%20Application%20Security/MAS1.png?width=409&height=168&name=MAS1.png)
Native mobile apps provide a superior user experience but escape your control once downloaded, opening possibilities for exploitation.
If you work in highly regulated sectors, your apps will contain financial, health, personal or similarly sensitive data. Off-the-shelf vendor solutions are not enough and breaches don’t just threaten to halt your revenue streams, they can destroy your reputation and lose you customers.
The result? Multi-layered, trusted security that protects the integrity of apps, constantly watching for any potential threats, enabling proactive action, and ensuring advanced security mechanisms cannot be cheated.
/Mobile%20Application%20Security/MAS2.png?width=409&height=168&name=MAS2.png)
Native mobile apps provide a superior user experience of native apps but escape your control once downloaded, opening possibilities for exploitation. Unauthorized access to sensitive information on mobile devices can not only make customers and businesses vulnerable. It could pose national security risks. If a passport stored in a digital wallet is compromised, it affects the ability of border force agents to correctly identify someone crossing the border. Bad actors could illegitimately cross nations or genuine citizens could be denied entry. Mobile app protection is not just a question of convenience. It is about managing all modern security risks to keeping sensitive data safe. If you work in highly regulated sectors, your apps will contain financial, health, personal or similarly sensitive data. Default vendor solutions are not enough and breaches don’t just threaten to halt your revenue streams, they can destroy your reputation and lose you customers. Work with the global specialists to set threat parameters exactly as you wish and provide the highest levels of protection.
Our deep knowledge of the science of cryptography and security simplifies adoption of security best practices for your developers. This enables them to flex their artistic muscles and focus on form and function, creating beautiful digital experiences without being burdened by security compliance requirements.
Cryptomathic provides tools that:
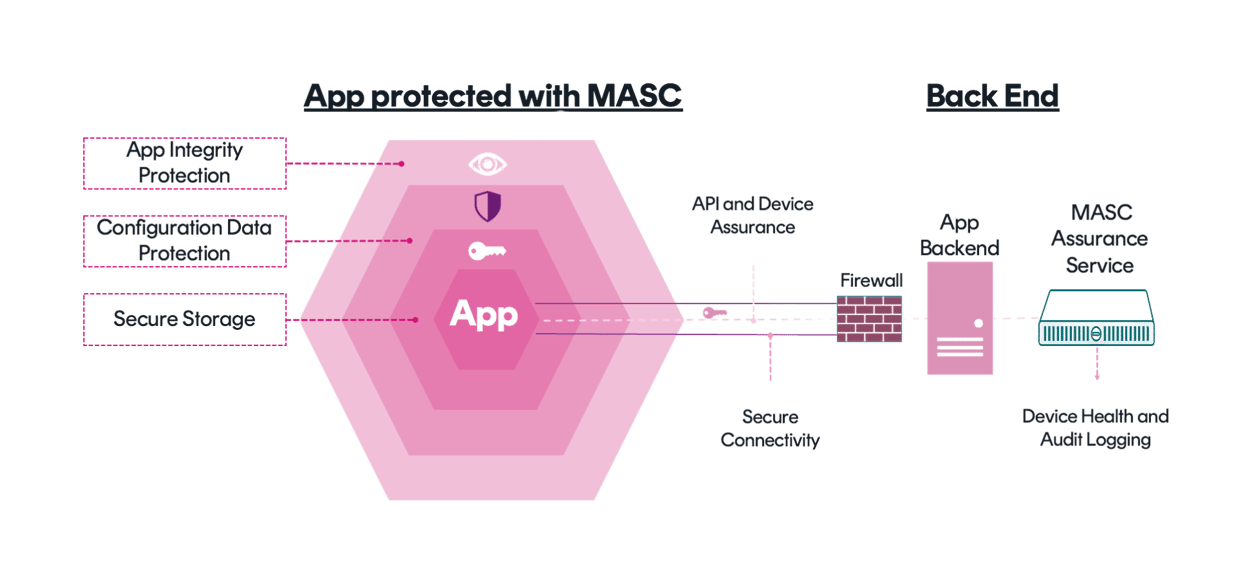
|
Secure Storage |
Configuration Data Protection |
App Integrity Protection |
|
|
|
|
Secure Connectivity |
API and Device Assurance |
Device Health Service |
|
|
|
Cryptomathic MASC is a security software development kit (SDK) for mobile apps on Android and iOS.
Five core components make MASC the leading mobile app defense solution available:
/Mobile%20Application%20Security/MASTAB201.png?width=208&height=138&name=MASTAB201.png)
/Mobile%20Application%20Security/MASTAB203.png?width=276&height=183&name=MASTAB203.png)
/Mobile%20Application%20Security/MASTAB202.png?width=300&height=199&name=MASTAB202.png)
Ensure the app only communicates with the intended system and maintains its own certificate store
Measures for securing connectivity include:
See how Cryptomathic Mobile App Security Core (MASC) works:
Governments worldwide are exploring and launching digital identity wallets, creating powerful and convenient gateways to services from healthcare, to payments, insurance and more.
These wallets are typically accessed via mobile devices. They enable quick access to certified ID documents, such as driving licenses, permits, health cards or passports, so consumers can quickly provide instant, irrefutable proof of their identity anytime, anywhere.
Unauthorized access to such sensitive information on mobile devices can not only make customers and businesses vulnerable. It could pose national security risks.
If a passport stored in a digital wallet is compromised, it affects the ability of border force agents to correctly identify someone crossing the border. Bad actors could illegitimately cross nations or genuine citizens could be denied entry.
/Mobile%20Application%20Security/MASTAB201.png?width=208&height=138&name=MASTAB201.png)
/Mobile%20Application%20Security/MASTAB203.png?width=276&height=183&name=MASTAB203.png)
As massive volumes of sensitive information flow through our mobile devices, are you prepared and confident to handle the increased risks of a digital-first society?
/Mobile%20Application%20Security/MASTAB202.png?width=300&height=199&name=MASTAB202.png)
You must make sure your digital ID and mobile wallet apps can:
Mobile apps are the most popular way for many consumers to access banking services, overtaking local branches, phone services and bank websites in recent years.
These mobile apps are required to be freely available on public servers. Unfortunately, this provides a playground for attackers to download and exploit weaker applications in their own time.
Cryptomathic’s Mobile App Security Core (MASC) provides comprehensive data protection and self-defending mechanisms with multiple, mutually reinforcing security layers.
MASC protects and tunnels the communications between the banking app and the server, while providing a library that enables the backend to monitor and respond in real-time to subversive activity occurring on the app and device.
/Mobile%20Application%20Security/MASTAB201.png?width=208&height=138&name=MASTAB201.png)
/Mobile%20Application%20Security/MASTAB203.png?width=276&height=183&name=MASTAB203.png)
Why banks trust the technical capabilities of MASC to protect their apps:
/BLOG.png?width=548&height=288&name=BLOG.png)
This blog runs through Mobile App Hardening and the techniques and best practices for implementing it.
/WHITE%20PAPER@2x.png?width=548&height=288&name=WHITE%20PAPER@2x.png)
Understand the threat landscape and how MASC's evolutionary security strategy can overcome such threats and provide 360º protections against attacks.
/PRODUCT@2x.png?width=548&height=288&name=PRODUCT@2x.png)
Mar 7, 2025 by Jan Lindquist
Mar 4, 2025 by Davin Cooke
Feb 13, 2025 by Boris Schumperli
Watch a recording of our webinar to understand the threats, risks, and vulnerabilities facing EUDI wallets and learn how to prevent spoofing, tampering, denial of service, information disclosure, and more.
WATCH THE RECORDING%20(1)-1.png)