- Home >
- TSM Solutions: 3rd Party SIM Card Management
Trusted Service Manager (TSM) is a relatively new role required in a mobile Near Field Communication (NFC) ecosystem. The core services a Trusted Service Manager offers, are the secure management and provisioning of the applications issued by service providers, such as banks, transport / ticketing authorities, merchants, or other application issuers. Provisioning performed over the air (OTA) includes, for example, the download, installation, personalization and life-cycle management of the applications to the secure element of the Near Field Communication (NFC)-enabled mobile phone. The SIM as a portable, secure and already existing smart card component will be the obvious secure element form factor for mobile phones. However, the Trusted Service Manager can support additional secure element form factors as well.
Since the first SIM supported NFC-enabled mobile phones entered the market during 2009-10, the management of the third party applications on the SIM cards needed to be planned and agreed between the different parties. The GlobalPlatform's Card Specification version 2.2 gives a good framework for this, but as the specification includes several options, the preferred ones need to be chosen and details agreed between:
- The Mobile Network Operator (MNO), the issuer of the SIM card,
- The Service Provider (SP) such as bank or transport operator issuing the applications, and
- The Trusted Service Manager (TSM), who provides services for both the Mobile Network Operator and Service Provider.
Integration of the Mobile Network Operator (MNO) and Trusted Service Manager (TSM) Systems
Since the SIM card is always issued by the MNO, certain integration work needs to be executed between the MNO and TSM systems and processes. There are various technical alternatives for constructing the interfaces between MNO platforms and third party TSM platforms in order to ensure a flawless and secure communication.
This article presents two aspects in interface design:
1) The interface between the TSM platform and MNO SIM OTA platform for over the air communications, and
2) Other interfaces required for a Near Field Communications ecosystem.
Such other interfaces include a "Security Domain Management" interface, i.e. an interface to enable the TSM to request so called token signing 3rd party TSM management of SIM card services from the MNO. The token signing service can be implemented as an online or offline service per NFC application and therefore the selected mode has an impact on the corresponding interface.
Security Domain Hierarchy
Security Domains (SD) are used for the management of Service Provider applications on a SIM card issued by the MNO. Security Domains can be established and managed in alternative ways and within different hierarchy models. Different Security Domain hierarchy models are presented in this article, and it should be noted that all models are applicable but the final selection of the model to be deployed must be made through joint discussion and planning between the MNO, Service Provider (SP) and TSM.
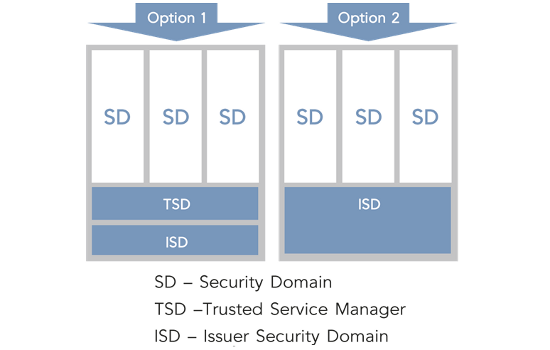
Security Domain Option 1
The first option for a Security Domain hierarchy is to have a dedicated Security Domain (SD) for the TSM usage - a TSD (Trusted Service Manager Security Domain). The TSD is associated to an Issuer Security Domain (ISD), which is managed by the issuer of the secure element, the MNO. If the Trusted Service Manager Security Domain is used, each Service Provider application is installed and personalized in a dedicated SPSD (Service Provider Security Domain), Properties and privileges of the TSD define the TSM's capabilities on the SIM card.

Security Domain Option 2
A second option is that Service Provider Security Domains (SPSDs) are associated directly to an Issuer Security Domain (ISD). Final architecture of the Security Domains and their use needs to be undertaken by the issuer of the secure element (the MNO), in mutual understanding with the SPs issuing their applications to this platform. The TSM should be able to support all the different alternatives. Main options for SD management hierarchy are described below.
It is important to understand that the underlying business agreements create the foundation for the service provisioning for all the alternatives. Naturally, the SIM cards must also support the chosen features.
Security Domain Option 1 with Delegated Management
The following figure highlights the interfaces and interactions between the TSM platform (in the picture Venyon Trusted Service Platform) and the MNO platforms for a setup where delegated management is configured for the TSM Security Domain (SD) and where the TSM does not have its own Remote Application Management (RAM) keys needed for creating a direct Bearer Independent Protocol (BIP) channel to the SIM card.
 In this setup the TSM always communicates through the MNO SIM platform. Additionally, the MNO needs to sign the tokens enabling the applet download into the TSM SD or alternatively into the Service Provider SD (SPSD), if a TSM SD is not used.
In this setup the TSM always communicates through the MNO SIM platform. Additionally, the MNO needs to sign the tokens enabling the applet download into the TSM SD or alternatively into the Service Provider SD (SPSD), if a TSM SD is not used.
Although the communication goes through the MNO SIM platform and is delegated, the security is fully protected between the TSM platform and TSM SD / SPSD for the download and personalization of SP applets, as well for any life-cycle management services for the applets.
Security Domain Option 1 or Option 2 with Authorised Management
In the authorised management alternative the TSM is capable of content management without specific tokens from the SIM issuer (MNO). In an SD Option 1 scenario the TSM can, for example, create new Security Domains (associated to the TSD) and populate their keys under a secure channel opened with the TSD. For an SD Option 2 hierarchy there is no TSD and the SPSD(s) is therefore associated directly with the ISD.
The picture below highlights the interfaces and interactions between the TSM platform (in the picture Venyon Trusted Service Platform) and the MNO platforms for a setup where authorised management is configured for the TSM SD and where the TSM does not have its own RAM keys needed for creating a direct BIP channel to the SIM card. For an SD Option 2 hierarchy there is no TSD and the SPSD(s) is therefore associated directly with the ISD.
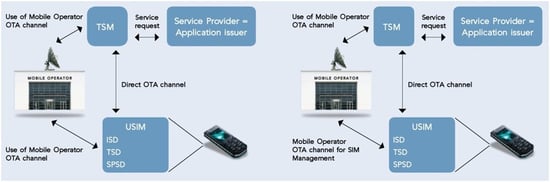
In this setup the TSM will always communicate through the MNO SIM platform.
Again the security is fully protected between the TSM platform and TSM SD / SPSD for the download and personalization of the Service Provider applets as well for any life cycle management services for the applets, using the MNO SIM platform.
Trusted Service Manager With its Own Remote Application Management (RAM) Keys
If the TSM is given the TSM specific RAM keys, it can create a direct BIP channel to the SIM card without routing it through the MNO platform. If the MNO needs to sign the tokens enabling the applet download into the TSM SD / SPSD, it will use the delegated option. If token signing is not required, the authorised model will be used.
In both these models the security is fully protected between the TSM platform and the TSM SD / SPSD for the download and personalization of SP applets as well for any life-cycle management services for the SP applets.
Cooperation and Dialogue Needed Between All Stakeholders
Technical options are now quite well defined and Mobile Operators and Service Providers can choose the most appropriate ones for their implementation. It is however important to realize that the underlying business agreements create the foundation for the service provisioning for all of these alternatives. Therefore close cooperation is needed to settle the outstanding business and technical issues. By doing so, all stakeholders can build the sustainable long-term mobile contactless business case enabled by NFC.
Contact us for further information.
Originally published in Cryptomathic NewsOnInk, 2009