2 min read
EUDI Wallets & Trust Services: The Future of Digital Identity and Signatures in eIDAS 2
In our Part 1 blog, we explored how eIDAS 2.0 marks a transformative shift for Trust Service Providers (TSPs) across Europe. In this follow-up, we...

2 min read
In our Part 1 blog, we explored how eIDAS 2.0 marks a transformative shift for Trust Service Providers (TSPs) across Europe. In this follow-up, we...

3 min read
The evolution from eIDAS 1to eIDAS 2 brings profound changes for the European digital trust ecosystem — notably, an emphasis on interoperability,...

1 min read
This week Cryptomathic launched a new remote qualified sealing offering.

2 min read
There has been a lot of buzz about the advancements in quantum computing recently from Google, Nvidia, and Bill Gates.

3 min read
With the increasing adoption of mobile banking and payment apps, financial institutions face greater challenges in securing cardholder data. The...

3 min read
Whether you’re tapping to pay at a coffee shop, or sending money to a friend, or even providing identification, mobile wallets have become the go-to...

3 min read
For an internal event atCryptomathic, we invited some our clients from the financial and trust service sectors to share their insight on future...

4 min read
The primary objective of the PCI MPoC (Mobile Payment on COTS) standard is to ensure that robust security mechanisms are in place for secure mobile...

1 min read
The new partnership aims to create a seamless process for companies to discover, inventory, and manage cryptographic assets.

3 min read
The Digital Operational Resilience Act (DORA), set to become fully enforceable on January 17, 2025, represents a significant evolution in the...

1 min read
Cryptomathic is thrilled to welcome Marianne Van Der Pluym to the team as Global Head of Partnerships. With her extensive experience and proven track...

4 min read
Secure elements (SE) on Android and secure enclaves on iOS have emerged as trusted hardware-backed solutions for storing and protecting sensitive...

3 min read
Cryptomathic is thrilled to announce a significant enhancement to our Mobile App Security Solution (MASC) offering with Insights Service. Insights...

4 min read
The choice of app protection should not be taken lightly. Modern applications face numerous threats that evolve alongside advancements in...

1 min read
We are delighted to announce the launch of Obsidian payment platform, a cutting-edge digital payments solution for issuers designed to meet the...

7 min read
Short-lived certificates play a vital role in current infrastructures, finding a suitable quantum-resistant alternative to the currently used...

2 min read
Two foremost software security experts and pioneers in cryptographic agility and post-quantum cryptography join forces to offer comprehensive,...

4 min read
As the European Union solidifies the framework for the EUDI (European Digital Identity) wallet, the certification process outlined in the...

6 min read
This article evaluates the implementation options for the Signature Activation Module (SAM) in the context of eIDAS 2. Based on this analysis we...

2 min read
Mobile phones are increasingly vulnerable to hacking and fraud, presenting significant challenges for securing sensitive applications like the EUDI...

2 min read
The EUDI wallet reference implementation serves as a practical guide for developers to create secure digital identity management solutions based on...

3 min read
The EUDI (European Digital Identity) wallet solution reference architecture (ARF) is designed to provide a secure framework for managing digital...

2 min read
To deliver trust services, managing user´s identities and access is paramount. eID schemes and trust service providers all require IdP solutions for...

3 min read
North America is catching up fast to the open banking initiatives that are currently thriving across Europe, South America and Asia Pacific. As...

1 min read
Cryptomathic is delighted to welcome Edmundo Diaz as its new Sales Director for Southern Europe, Africa and Latin America (LatAm). Edmundo’s...

1 min read
Data security can be complex, but it's essential in today's business world, especially when using cloud services. One effective approach is adopting...

1 min read
Cryptomathic further bolsters its leadership team, welcoming Davin Cooke as Sales Director for the company’s North American operations.

2 min read
In today's fast-evolving digital landscape, robust key management has become an essential part of securing sensitive data and communications. The...

1 min read
Cryptomathic’s Mobile App Security Core (MASC) delivers the highest levels of security, protection and privacy for citizens using the app

4 min read
Today’s cars are computers on wheels which operate in a connected world and ecosystem of other cars, roadside infrastructure, and the cloud. Car...

1 min read
Cryptomathic is delighted to announce the appointment of Anna Russell as Chief Revenue Officer (CRO).

4 min read
Cryptomathic solutions support your financial institution towards compliance. The financial sector is increasingly dependent on technology and tech...

1 min read
signer 6 enables future-proofed, scalable digital signing to support the upcoming european digital identity wallet (eudi) We are delighted to...

2 min read
Cryptomathic guides you towards compliance. EU Directive 2022/2555 on Network and Information Systems, also known as NIS2, entered into force on Jan...

4 min read
In today's digital landscape, ensuring the security of your mobile applications is paramount. Cryptomathic's Mobile App Security Core (MASC) is at...

2 min read
PCI have recently released the new standard and compliance program for Mobile Payments on Commercial off-the-shelf devices (MPoC). This blog is the...

2 min read
The European eIDAS regulation, short for the Electronic IDentification, Authentication and Trust Services Regulation, was created in 2014 to ensure...

2 min read
What is Mobile Application Hardening? Mobile application hardening refers to the process of securing mobile applications against various threats and...

2 min read
On July 17, 2023, the National Institute of Standards and Technology (NIST) announced a new set of 40 candidates to compete in their Post-Quantum...

3 min read
In today's digital era, banks are increasingly leveraging cloud and multi-cloud environments to drive operational efficiency. However, the security...

2 min read
The European Commission, as part of the eIDAS 2.0 proposal promotes the European Digital Identity Wallet (EUDI Wallet) as an app that enables...

3 min read
AWS Key Management Service (KMS) has long provided cryptographic services to safeguard your AWS resources. This involves generating and managing keys...

3 min read
Believing that more cybersecurity solutions increase safety is a common misconception. An overload of security measures can ironically generate more...

4 min read
When organizations make the strategic decision to shift their applications and infrastructure onto the cloud, they face a myriad of challenges. These...
7 min read
The ubiquity of mobile applications has made them part of our day-to-day lives, but with the increased use comes the risk of potential security...

7 min read
Were I to ask you what a handwritten signature looks like, with an air of confidence will you grab a pen and scrawl your name on a piece of paper,...
4 min read
The European Digital Identity Wallet (EUDI Wallet) is at the forefront of the European Commission's eIDAS initiative to establish a secure and...

4 min read
Quantum computers offer potential transformational power for organizations dealing with complex computational problems in various industries such as...

4 min read
Along with the increased convenience and security offered by digital payment technology, many consumers are now showing greater interest in...

5 min read
The zero-trust approach to enterprise cybersecurity assumes that no connections to corporate systems and networks should be trusted. It requires...

4 min read
Cryptomathic Mobile App Security Core (MASC) is a comprehensive security software solution for the European Digital Identity (EUDI) wallet, eID apps,...

1 min read
The European Digital Identity Wallet (EUDIW) has the potential to serve as a comprehensive identity gateway, enabling individuals to manage their...

3 min read
The adoption of cloud computing has altered the approach organizations take toward security. Rather than concentrating on securing the perimeter of a...

4 min read
Zero Trust security is a concept that has been discussed extensively. However, there are many different interpretations of what it means. Some...

2 min read
Cryptomathic is excited to announce that we have partnered with fidentity, an expert in online identity verification, to enable automated identity...

6 min read
Itemizing the potential risks of the European Digital Identity (EUDl) Wallet scheme is a complex task that involves assessing the attack surface of...

3 min read
The European Digital Identity wallet (EUDI wallet) is proposed by the European Commission to provide a secure, safe and standardized digital identity...

5 min read
Merchants must remain vigilant against fraud and ensure they have the necessary tools to combat it. Failure to do so may render their fraud detection...

4 min read
The recent instability of a major bank that catered to US tech startups caused concern for several prominent tech companies and venture capitalists,...

5 min read
Under the GDPR, organizations must take appropriate measures to protect personal data from unauthorized access, use, disclosure, or destruction. One...
6 min read
The European Digital Identity (EUDI) Wallet aims to offer digital wallets to all EU citizens and businesses for identification purposes and document...

5 min read
Mobile apps and mobile software components are rarely stand-alone as they frequently perform their most important operations on various backend...

4 min read
Large-scale quantum computing is coming soon, and with that comes new cybersecurity threats. One of these threats is "steal now, decrypt later,"...

2 min read
Hardware security modules (HSMs) are physical devices that provide cryptographic functions such as encryption/decryption and digital signing. They...

5 min read
Each year, various events within the cybersecurity industry have a significant impact on the industry, leading experts to predict an increase in the...

2 min read
With post-quantum technology having the potential to trigger a new wave of cyber threats, we identify 10 steps that organizations should take to...

4 min read
The UK's relationship with the EU has been tumultuous in recent years, especially in the wake of Brexit. With regards to digital identities, former...

4 min read
EMV Personalization of a payment card is the process of writing data to the card in order to make it ready for use. This includes loading the card...

5 min read
The European Commission promotes the European Digital Identity wallet (EUDI wallet) as part of its effort to digitize the economy and help foster...

4 min read
Companies who use Amazon Web Services (AWS) often choose to do so because of its scalability, ease of use and lower costs than other services or...

2 min read
Security experts from the National Institute of Standards and Technology (NIST) have declared Ascon - a group of cryptographic algorithms - as the...

3 min read
Keeping data safe in the Cloud has always been a concern for users, hence the need for encrypting data. With more businesses taking advantage of what...

4 min read
The “Four Corners” model, also called the “Four Party Scheme”, is utilized in almost all standard card payment systems across the globe. Here, we...

3 min read
When it comes to preparing for post-quantum computing, the legacy mechanisms for effective implementation, integration, and management of...

4 min read
Digital transformation has been a critical focus for businesses and institutions prior to the pandemic. Digital documents and e-signatures are a...

3 min read
The AWS cloud is enjoying increasing popularity with its very high levels of scalability, durability, and availability. It releases companies from...

8 min read
Vehicles today come with an array of convenience and safety features driven by software. This means that the cybersecurity of these vehicles must now...

3 min read
EMV Personalization is a process used to get card data into cards, mobile phones, and wearables. The process includes a variety of complicated...

3 min read
In today’s dynamic business landscape, companies need to be agile with their cloud processes to remain competitive. But at the same time, they must...

3 min read
Cloud storage via AWS Storage Services is a simple, reliable, and scalable way to store, retrieve and share data. As a third-party cloud vendor, AWS...

3 min read
The 2020 Oracle and KPMG Cloud Threat Report focuses on the key risks and challenges organizations face as they implement and maintain cloud...

3 min read
This article discusses how prepared companies are for quantum computing cybersecurity risks based on a recent Deloitte poll and what the current...

5 min read
To bank safely online, you need additional mobile app security mechanisms that go beyond standard OS security features. In this article, we take an...

3 min read
As the use of mobile phones for mobile banking and payment applications increases, so too do the security threats. Most smartphones use only two...

4 min read
Among all the various key block formats, the TR-34 format is undoubtedly one of the most sophisticated. The TR-34 norm is an implementation of the...

3 min read
This article sheds light on the intersection of legal and technical aspects when hosting data on AWS as a European company.

3 min read
On April 19, 2022, information about a severe vulnerability in recent versions of Java shook up the security community.

3 min read
This article proposes a few answers to a series of frequently asked questions (FAQs) about key blocks and their use with PCI.

3 min read
As defined by Regulation (EU) No 910/2014 (eIDAS), which took effect on 1 July 2016, an electronic signature creation device is software or hardware...

5 min read
Today's businesses rely heavily on cryptography to authenticate people and processes, secure communications, and safeguard critical data.

4 min read
In the “four corner model”, acquirers are apparently the less active party as their role seems ‘only’ to forward the transaction flow originating...

3 min read
Mortgage fraud is a serious crime. Once executed and signed, a mortgage deed is a legally binding contract. The responsibility of trying to prove...

5 min read
Achieve Non-Repudiation of Origin (NRO) and Non-Repudiation of Emission (NRE)

5 min read
This article is meant to be an introduction to the different types of cryptographic keys that are used to protect digital applications in encryption...

3 min read
An issuer is one of the corners in the ‘four corner’ model. An issuer is a financial organization (e.g. a bank) that produces payment cards and...
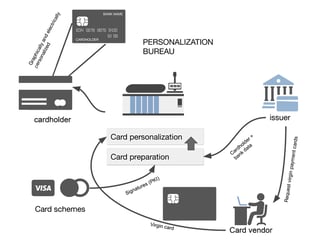
3 min read
The EMV personalization data processing in itself is not the topic of this article, we will instead focus on the cryptographic schemes involved in...

2 min read
A key block is a unique piece of cryptography that is used to protect cryptographic keys while they are being sent over networks that might not be...

4 min read
IBM’s mainframe computers have been a rock-steady part of banks’ security infrastructure for many years. Originating from the local data-center...

3 min read
This article explains the digital Signature Activation Protocol (SAP) in the context of eIDAS-compliant central signing. It sheds light on its...

4 min read
The use of mobile payments is expected to continue to rise and become the second most popular payment method after debit cards by 2022. Analysts...

4 min read
National digital signature schemes that utilize remote electronic signature technology can achieve very high usage rates, whereas Trust Service...

3 min read
The IBM Common Cryptographic Architecture (CCA) is a cryptographic platform providing several functions of special interest for securing financial...

2 min read
Just a month ago, NIST announced its selection of three digital signature algorithms and one key establishment mechanism (KEM) for future use in...

3 min read
Traditionally, end-to-end lifecycle key management was achieved through inefficient paper-based procedures and highly resource intensive tasks...

3 min read
Encryption has become the most essential part of securing data online. The biggest headache to the Cybersecurity industry is a data breach. The last...

3 min read
With the ever increasing number of online services and electronic transactions, business owners are becoming ever more dependent on the use...

2 min read
In this article, we proposeWhat-You-See-Is-What-You-Timestamp (WYSIWYT) as an attractive alternative to Qualified Electronic Signatures, for certain...

5 min read
Certain industries have a duty to protect confidential information, as well as a requirement for authentication - proving that a document was sent by...

3 min read
An over five-year-long process has come to a preliminary end: On July 5, 2022, NIST issued the long-awaited announcement of the winners of Round 3 of...

2 min read
There are several types of key block formats used in different industries, especially the retail banking industry. The systems that use these key...

3 min read
With the introduction of PSD2, banks are forced to provide third party payment service providers (PSPs) with access to the bank’s customers’ account...

5 min read
Many organizations struggle with cryptographic key management for multiple reasons. However, these pain points can be resolved with the right tools.

4 min read
Cardholders (or consumers) are one of the corners of the ‘four corner’ model in the payment card world. Here we take a brief look at the payment...

2 min read
This article describes a model that could enable an electronically signed document to be printed out and used as an original in legal proceedings, in...

3 min read
Code obfuscation is one of the most effective techniques for protecting sensitive data in mobile banking and payment apps. However, it's not always...

5 min read
This article aims to demystify electronic signature UK law and explain how it supports all types of electronic transactions in accordance with UK...

5 min read
Here we look at what it means to “bring your own key”, “control your own key” and “hold your own key” and what the differences are between these...

8 min read
PSD2 breaks up the ways in which banks do their business, by forcing them to open up their APIs. By doing so, PSD2 challenges the way in which data...

3 min read
Cryptography is the backbone of data security technology. In this article, Jo Lintzen, MD at Cryptomathic Inc. explains the preparations for...

3 min read
The demand for remote digital signatures to enhance security and customer experience continues to grow across the EU, as the banking and financial...

2 min read
One aspect of key management is dealing with what happens when a symmetric cryptographic key is no longer needed. The section ‘Key Replacement,...

3 min read
The eIDAS regulation sets the standard for electronic identification, electronic signatures, and trust services. It paves the way for delivering...

3 min read
The eIDAS Regulation lays the groundwork for creating a robust digital identity framework. The idea is to provide EU citizens with a secure, robust...

3 min read
This article addresses some of the challenges of symmetric cryptography as applied in banks, describing how it works and what are its unbeaten...

2 min read
The ANSI X9.24-1-2017 standard defines the requirements for the loading of key components or shares, and the loading of cleartext keys. The loading...

4 min read
Last month, one of the three NIST finalists for post-quantum signature schemes received its final nail in the coffin: Ward Beullens, a PostDoc at IBM...

2 min read
The eIDAS Regulation (No 910/2014) (EU eIDAS) came into force in 2016. It created a Europe-wide legal framework for electronic identification,...

5 min read
There is no question that quantum computing is coming. However, organizations need to question themselves as to whether they will be vulnerable to...

2 min read
Most current public-key cryptography (asymmetric) algorithms are vulnerable to attack from large-scale quantum computers. In its efforts to...

2 min read
Maybe you have wondered where our logo comes from and what it actually means. If you have, we hope the following will answer these questions. Just as...

2 min read
Attacks on mobile banking and payment applications frequently begin with the use of an emulator for the mobile operating system, where the targeted...

6 min read
The ever-growing number of applications and uses for mobile devices has long been a hot topic. Using mobiles to electronically sign transactions and...

2 min read
The European Union is leading the way in the move towards the creation of a single digital market. There are many advantages a digital business has...

6 min read
With the growing need for cryptography solutions to protect digital assets and communications, the ever-present security holes in modern computer...

2 min read
Microsoft’s Azure Key Vault Managed HSM allows customers to safeguard their cryptographic keys for their cloud applications and be...

3 min read
This article looks at some reasons for popularity of the IBM mainframe platform in the banking sector and touches upon its limitation for...

2 min read
A number of serious security vulnerabilities, collectively known under the names of “Meltdown” and “Spectre” [1][2], have recently been discovered in...

3 min read
The European Interoperability Framework (EIF) adopted in 2017 is the primary thrust in the EU’s effort to improve the efficiency of public service...
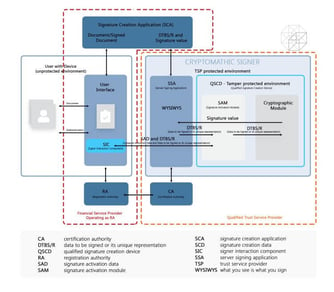
3 min read
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...

4 min read
This article explains the four primary cloud KMS pattern combinations and which are best suited for use with Cryptomathic’s Key Management System...

3 min read
A study published in early 2018 by the European Union Agency for Network and Information Security (ENISA), revealed that 90% of the respondents...
3 min read
The PCI Council requires most actors of payment networks to implement ANSI X9.24/TR-31-compliant key blocks to wrap and securely transmit, transfer,...

5 min read
RSA, a short recap In a public key scheme, and for the sake of simplicity, assume a public scheme based on encryption-decryption (as opposed to e.g....

2 min read
User interface design and usability are the deciding factors in attaining a good user experience for most IT deployments, including key management...

3 min read
Bring your own key (BYOK) is a popular term relating to key management for cloud applications. However, a lack of standardization makes it confusing...

3 min read
Banks continue to feel the profound transformational effects that digital technologies have on their business. This can be seen in the creation and...

4 min read
This article discusses how tokenization may reduce false declines with credit card transactions that could negatively impact merchants.

3 min read
A crypto-abstraction layer (CAL) is, in its most general sense, an application programming interface (API) - also known as a library- that hides...

2 min read
This article proposes answers to a series of frequently asked questions (FAQs) about key blocks.

3 min read
Hardware Security Modules (HSMs) are used in all card payment systems (as well as various other applications that require strong security) to protect...

3 min read
As part of the global drive for digital transformation, legally binding digital signatures are at the forefront of many businesses’ ambitions to...

5 min read
Last week order for 186 double-decker trains was nullified due to a legal formality surrounding the Qualified Electronic Signature used to ink the...

5 min read
This article talks about how different factors and controls can affect the strength and effectiveness of a cryptographic system's security. It gives...

3 min read
The financial service industry has always been innovator in technology adoption. This is not surprising considering the nature of the industry with...

4 min read
Under pressure from sophisticated attacks and rising fraud, many B2C organisations of the financial industry are currently enhancing the static...

3 min read
This article briefly summarizes the symmetric cryptographic key utilization and storage requirements as described by the ANSI X9.24-1-2017 (part 1)...

2 min read
Great strides have been made in the retail banking and payments space via innovative financial technology products. However, in the corporate banking...

6 min read
Ever since the EU mandated the introduction of biometric ePassports containing fingerprints there has been a flurry of technology development and...

4 min read
MULTOS cards are being deployed in steadily increasing numbers and Cryptomathic is delighted to be involved in MULTOS projects across the globe....

3 min read
The IBM mainframe series (“z-series”) has become a backbone for security, privacy and resilience in a large share of payment and banking related...
3 min read
Thales Key Blocks are an essential cryptographic key wrapping format. In comparison to other key block formats, they are proprietary and only work...

3 min read
Banks and other financial institutions are playing a key role in countering global challenges like money laundering and terror financing.

2 min read
Banks and financial institutions must adhere to a rigorous set of security and regulatory practices to protect data, communications, and processes.

3 min read
The protection and secure management of cryptographic keys is crucial for ensuring that cryptography is used in the most effective way to keep data...

3 min read
In May 2021, researchers published two attacks on certified PDFs, which enabled unintentional and fraudulent modifications to be applied to signed...

4 min read
This article explores how Cryptomathic CKMS combines BYOK for the MS Azure Key Vault with banking-grade key lifecycle management; to address the...

4 min read
This article discusses key management methods for the IaaS Cloud model, and security problems to be dealt with because of its virtualization...

3 min read
The ultimate aim of regulations like eIDAS is the creation of a true Digital Single Market (DSM). eIDAS plays its role by providing the necessary...

3 min read
With each passing year, the volume of international trade in goods and services keeps rising. With all of this trade, however, comes an associated...

4 min read
Recent global events have demonstrated that high-profile hackers and state-sponsored security breaches have been steadily increasing since 2020. It...

2 min read
How can keys be securely exchanged over potentially unprotected channels? The answer to this question is “key blocks”. A key block is an essential...

3 min read
The growth of electronic identification systems has been different for each European country during the past several years. European countries have...

3 min read
Over the last 10 years, enterprises have moved on from decentralized and distributed key management to centralized key management systems to provide...

5 min read
A key management system is a critical component in achieving PCI DSS compliance for a banking institution. It involves implementing a crypto system...

3 min read
What You See is What Your Sign (WYSIWYS) is a term that is used to describe an enhanced level of data integrity within a digital signature system....

4 min read
The cloud services provided by Microsoft Dynamics 365 are gaining rapid market share in the banking world. A burning question for the security...

4 min read
This article outlines the importance of code signing and describes a centralized approach for securing and streamlining the code signing process...

3 min read
ATM Remote Key Loading has become a common practice in the industry. Yet managing the top-level keys to establish trust between the Host and the ATM...

3 min read
This article discusses the misuse of X.509 certificates and keys in the SolarWinds attack and how Cryptomathic CKMS and CSG could help protect...

3 min read
This article explains some of the cryptographic key management tasks involved in demonstrating and proving compliance to acceptable standards, and...

3 min read
The Delegated Regulation on Regulatory Technical Standards (RTS) by the European Commission aims to facilitate Strong Customer Authentication (SCA)...

3 min read
The Key Management Interoperability Protocol standard intends to provide interoperability across various key management environments and hence to...

3 min read
The CEF building blocks of the digital service infrastructure, as defined under the Connecting Europe Facility (CEF), cover essential components like...

2 min read
Since the announcement of the SolarWinds supply chain attack, intensive analysis has been done by Crowdstrike, FireEye (with additional details),...

3 min read
In this article, we look at the process of a keyshare generator and key derivation as described by the ANSI X9.24-1-2017 standard. This process is...

5 min read
This article discusses the concerns surrounding key management for cloud environments and how Cryptomathic addresses them by bringing banking-grade...

2 min read
People often use the terms e-signature and digital signature interchangeably. However, they aren't the same thing. Everything from the processes that...
5 min read
An investigation conducted by "Which?", a consumer watchdog group based in the UK, found serious vulnerabilities in the security of banking security...

2 min read
We are constantly reminded by news stories how complex it can be to secure mobile banking and payments apps. A recent study has found that 11%...

3 min read
The term PAdES stands for PDF Advanced Electronic Signatures. It refers to a group of extensions and restrictions that are used with PDF and ISO...

3 min read
Unlike other operating systems like Windows, Linux, or OSX, both Android and iOS operating systems are usually shipped with built-in user rights...

3 min read
The rise of quantum computing is expected to have significant impacts on both financial and technological considerations when evaluating...

3 min read
With the ever-growing number of electronic transactions and documents, the use of digital signatures make it possible to trust and act upon these...

4 min read
In this article, we will discuss the Certificate Authority (CA) in the context of eIDAS and what is required of this entity in ensuring the integrity...

4 min read
Considering the COVID-19 impact on digitalization, EBA’s updated Guidelines on ICT and Security Risk Assessment will help focus on priority areas,...

3 min read
Securing data and keeping it private is essential for many organizations and institutions, including banks or ministries, where data security and...

4 min read
The PSD2 Directive opens a considerable market for new solutions in e-banking, account information services and payment initiation services.

2 min read
The European Banking Authority's (EBA’s) new ICT and Security Risk Management Guidelines provide guidance for cybersecurity requirements for...

4 min read
Even in small-scale environments, managing cryptographic relationships and crypto key lifecycles can be difficult. The list of barriers to success...

5 min read
Open banking can offer opportunities for retail banks that are faced with competition from newcomers to the banking and finance industry. For those...