3 min read
Why BYOK is Essential for Data Security and Privacy in the Cloud
Cryptomathic : 29. December 2022

- Home >
- Why BYOK is Essential for Data Security and Privacy in the Cloud
The 2020 Oracle and KPMG Cloud Threat Report focuses on the key risks and challenges organizations face as they implement and maintain cloud solutions. This article highlights some of the report's findings around the growing trust in the security of cloud offerings and asserts why maintaining control of your own critical keys should be considered best-practice when considering migrating to the cloud.
Public Clouds Are Considered More Secure
 In the past there has been concern over whether public clouds are secure that led to hesitation for adopting this technology.
In the past there has been concern over whether public clouds are secure that led to hesitation for adopting this technology.
Yes, there have been well-publicized incidents involving public cloud data loss. There is, however, growing sentiment among those surveyed that the level of security provided to public cloud environments is now better than what can be provided to on-premises data centers.
40% of those surveyed for the 2020 Cloud Threat Report viewed the security of public clouds to be well-above what they could provide to their on-premises environment.
This represents a 13% increase since last year of how the security of public clouds is positively viewed.
Even though there is an increase in sentiment that public clouds are secure, some concern remains about trusting cloud service providers, specifically the handful of providers that hold the greatest share of the market. Out of those IT professionals surveyed, 81% were concerned about the potential for complacency, while 80% also expressed concerns that the cloud service providers they work with will soon become competitors in their core markets.
Indeed, many organizations have become comfortable with the security public clouds offer. However, they want their CSPs to remain vigilant and committed to strong cybersecurity measures.
Business-Critical Applications are Moving to the Cloud
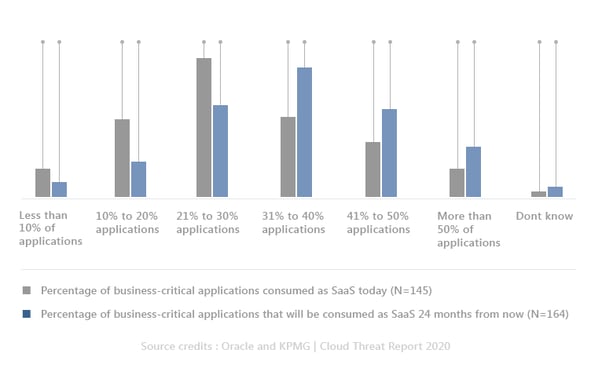
Nearly 9 out of 10 organizations who participated in Oracle and KPMG’s 2020 study are currently using software-as-a-service (SaaS). However, behind this impressive statistic is the current use of SaaS for office productivity and collaboration and most notably, a planned increase in using SaaS for business-critical applications. It is expected that there will be a 9% increase over the next 24 months of organizations shifting to SaaS for their business-critical applications.
As more businesses move to SaaS for their business-critical applications, it is safe to say that these organizations are increasingly comfortable with the security provided by cloud service providers. More businesses are trusting SaaS and the cloud for mission-critical applications that are the backbone of their operations, including:
- Enterprise resource planning (ERP)
- Customer relationship management (CRM)
- Human capital management (HCM)
- IT service management (ITSM)
The graphic below illustrates the percentage of SaaS business-critical applications today versus the percentage that is expected to exist within 24 months.
Encryption and Key Management
 Along with the cloud, the market for encryption is growing, and with more encrypted data we have more encryption keys to manage.
Along with the cloud, the market for encryption is growing, and with more encrypted data we have more encryption keys to manage.
As cryptographic keys underpin the security of applications and data on-premises, in the cloud, and in hybrid environments, properly managing their lifecycle is fundamental.
Encryption is only effective if you protect your crypto keys, and that is where hardware security modules (HSMs) and centralized Key Management Systems (KMSs) come into play.
HSMs protect critical cryptographic keys in a dedicated, hardened, hardware-based appliance that establishes a root of trust over your keys, your applications, and your data, whereas a KMS should control the lifecycle these keys.
Consequently, as organizations take advantage of the cloud to better serve their customers, they must keep in mind that loss, theft, or misuse of even a single critical key can have significant impact on their organizations, including the need to issue breach notifications, loss of revenue, falling share prices, and serious reputational damage.
Mitigate Security Risks with BYOK
To assure sound governance, compliance and internal controls, businesses need to maintain control over their cryptographic keys. Using “Bring Your Own Key” (BYOK) is crucial for mitigating ICT and security risks as it allows organizations to keep control of their critical keys while taking full advantage of the efficiencies that the cloud promises.
Another advantage of BYOK is that the customer does not risk being caught in a cloud vendor lock-in. Getting data out, e.g., when moving to a different cloud or into a different subscription service, can be a tedious, time-consuming and consequently costly process without BYOK.
As applications run, encryption protects data whether it is at rest in the database, in transit between data centers or user devices, or at public endpoints through TLS. When the right key management system is used for BYOK, a business’s data in the public cloud cannot be accessed by others, including third-party employees. The concept of BYOK also ensures that even the cloud service providers cannot gain access to these critical keys in unencrypted form and, therefore, it can provide further protections against insider attacks or even external government interventions.
References and Further Reading
- Cloud Threat Report 2020 (2020), by Oracle Corporation & KPMG International Limited
- Selected articles on Bring Your Own Key (2017 - today), by Matt Landrock, Stefan Hansen, Ulrich Scholten and more
- Selected articles on Key Management in the Cloud (2017-today) by Edlyn Teske, Matt Landrock, Rob Stubbs, Stefan Hansen, Ulrich Scholten, Joe Lintzen and more
-
NIST SP800-57 Part 1 Revision 4: A Recommendation for Key Management (2016) by Elaine Barker
-
Selected articles on Key Management (2012-today) by Ashiq JA, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
-
CKMS Product Sheet (2016), by Cryptomathic
