3 min read
Strong Customer Authentication Under PSD2: EBA Insights
Cryptomathic : 20. September 2020
- Home >
- Strong Customer Authentication Under PSD2: EBA Insights
A fundamental objective of the Revised Payment Services Directive (PSD2) has been to reduce the risk of fraud to the maximum extent possible and ensuring security for electronic payment transactions.
PSD2, along with the Regulatory Technical Standards (RTS), defines Strong Customer Authentication as an “authentication based on the use of two or more elements categorised as knowledge (something only the user knows), possession (something only the user possesses) and inherence (something the user is) that are independent, in that the breach of one does not compromise the reliability of the others, and is designed in such a way as to protect the confidentiality of the authentication data”.
The broader financial services industry and their partners have been working towards implementing these guidelines, but as with most new directives or guidelines, there have been some teething issues. Industry participants have to balance the cost of implementation, the performance impact in terms of delays and accuracy and the overall user experience of any such solutions. While at the same time they also have to be compliant with the basic requirements for Strong Customer Authentication (SCA).
This fine balancing act has meant that not everyone has perfect clarity if the specific solution that they have on the drawing-board and which meets their unique constraints, also fulfils all the SCA constraints. The European Banking Authority therefore published its own Opinion on SCA elements in June 2019. The document provides a rather insightful look at what may constitute a compliant element in each of the three possible categories of inherence, possession and knowledge.
Inherence
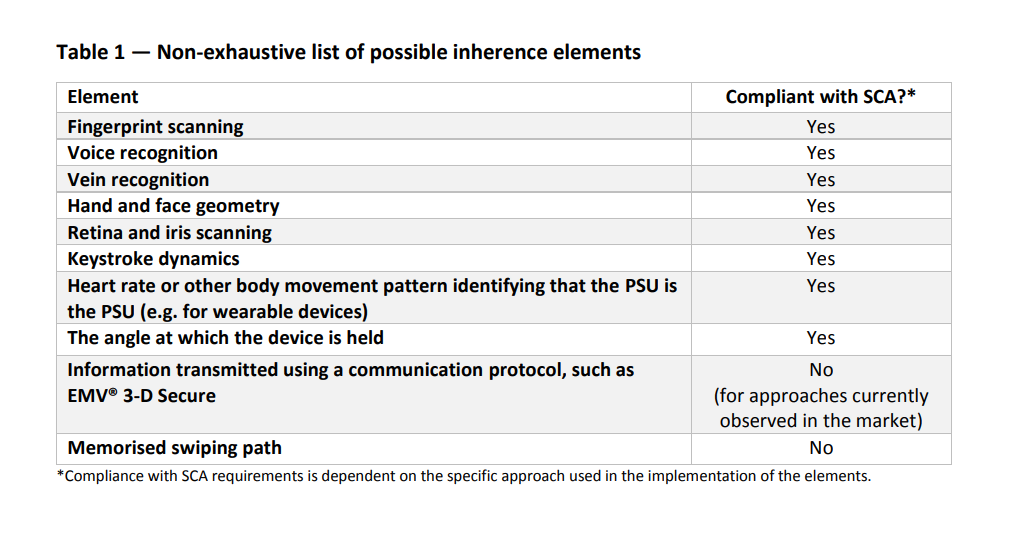
Inherence is “something the user is”. Looking at some of the rather uncommon elements in the accompanying list, it is not surprising that there was some ambiguity in the minds of solution providers as to their exact compliance with SCA requirements. It might also be seen as a sign that companies are thinking outside the box and this may eventually create a better and safer user experience for customers across the European Union. The EBA acknowledge inherence as the most innovative and fastest moving category amongst the various elements of SCA.
| Element | Compliant with SCA |
| Fingerprint Scanning | Yes |
| Voice Recognition | Yes |
| Vein Recognition | Yes |
| Hand and Face Geometry | Yes |
| Retina and Iris Scanning | Yes |
| Keystroke Dynamics | Yes |
| Heart rate of any other body movement pattern identifying the person | Yes |
| The angle at which the device is held | Yes |
| Information transmitted using a communication protocol, such as EMV* 3-D Secure | No (for approaches currently observed in the market) |
| Memorised Swiping Path | No |
Source: European Banking Authority
The EBA has stated its view on inherence as follows: “inherence, which includes biological and behavioral biometrics, relates to physical properties of body parts, physiological characteristics and behavioral processes created by the body, and any combination of these”.
Additionally, it is also clarified that the quality of implementation of any inherent approach will also be a factor in gauging its compliance with SCA constraints.
Biological and behavioral elements can provide varying degrees of certainty and the accuracy may very well depend on the exact approach taken as well. The focus on approach is relevant because there is always some subjectivity as to what really satisfies the condition of having a “very low probability of an unauthorized party being authenticated as the payer”. Because that is the condition that needs to be satisfied.
In Part 2 of this series, we will analyse EBA’s opinions on the other remaining categories of Strong Customer Authentication.
References and Further Reading
- EBA publishes an Opinion on the elements of strong customer authentication under PSD2 (June 2019), by the European Banking Authority
- EBA publishes an Opinion on the use of eIDAS certificates under PSD2 (December 2018), by the European Banking Authority
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- Selected articles on Authentication (2014-today), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner and more
- eIDAS webinar 1: Using electronic Identification, Authentication and trust Services for Business (2018), by the European Commission
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission
- Proposal for a DIRECTIVE OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL amending Directive (EU) 2015/849 on the prevention of the use of the financial system for the purposes of money laundering or terrorist financing (2016), by the European Commission
- REGULATION (EU) 2016/679 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (2016), by the European Parliament and the European Council
-
Proposal for a REGULATION concerning the respect for private life and the protection of personal data in electronic communications and repealing Directive 2002/58/EC (Regulation on Privacy and Electronic Communications), (2017), by the European Parliament and the European Council
- Revised Directive 2015/2366 on Payment Services (commonly known as PSD2) (2015), by the European Parliament and the Council of the European Union
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
-
DIRECTIVE 2013/37/EU amending Directive 2003/98/EC on the re-use of public sector information (2013) by the European Parliament and the Council
