- Home >
- eIDAS: What You See is What You Sign for Non-Repudiation
What You See is What Your Sign (WYSIWYS) is a term that is used to describe an enhanced level of data integrity within a digital signature system. Its purpose is to ensure that the content of a signed message cannot be altered, whether intentionally or accidentally (non-repudiation).
Primary Objectives of WYSIWYS to Consider
There are four primary objectives to consider with the use of WYSIWYS:
- It ensures that the integrity of the data-to-be-signed (DTBS) is protected and accurately rendered over a trusted viewer/interface before the user signs it under their sole control
- It provides a thorough audit trail that ensures non-repudiation of origin and emission
- The user has a way to validate the signature operation.
- The signature is elevated to the level of qualified electronic signature (QES)
Responsive to Cyber Threats
WYSIWYS works to thwart man-in-the-middle attacks (MITM), where the attacker secretly accesses and, in some cases, alters communications between two parties. Both parties mistakenly believe that they are communicating directly with each other.
WYSIWYS counters MITM attacks, including:
- Between Client (user’s browser) and the WYSIWYS server
- Between Client and the Signing server
- Man-in-the Middle in the browser
- Reusing federated identity credentials
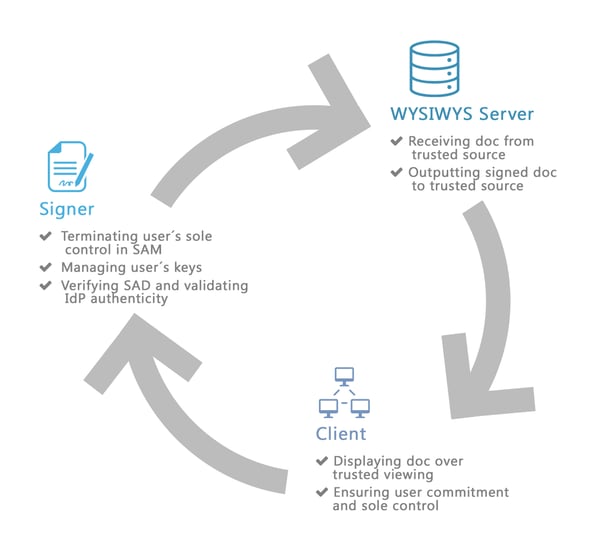
WYSIWYS Process in a Nutshell
As seen in the infographic below, the Cryptomathic Signer (Remote signature server):
- Terminates the user’s sole control in the Signature Activation Module (SAM)
- Manages the user’s keys
- Verifies the Signature Activation Device (SAD) and validates the authenticity of the identity provider (IdP)
The WYSIWYS Server:
- Receives doc from the trusted source
- Outputs signed doc to the trusted source
Client Side:
On the client’s side, the doc is displayed over a trusted interface/viewer in the browser. It also ensures the user's commitment and sole control over the signature.
Deployment Possibilities and Target Groups
Cryptomathic offers this technology to customers such as government departments, banks and trust service providers (TSPs). Depending on the strategic positioning and importance of the signing service within the customer's overall portfolio, Cryptomathic provides the infrastructure:
- On premise. In this deployment option, Cryptomathic’s technology is installed on-premise. The customer becomes a fully qualified trust service provider (QTSP) with full control and legal liability throughout the whole signing process and the signature & certificate life-cycle. This model is the preferred choice by certified trust service providers and governments.
Bigger banks or expansive banking networks might choose such a solution - either motivated by scale effects or by business model decisions. - Partially on premise. This model allows customers to offer remote signatures, where Cryptomathic operates the back-end signature services under SLA on the institution’s behalf; the institution assumes a limited role of a TSP. Through this arrangement, the financial institution will significantly reduce the workload of operative tasks as compared to the full TSP model, but remains in control of and legally liable for the whole process.
This model is the typical choice of banking networks or cooperatives, benefiting from the pooled and centrally managed services in the Cryptomathic cloud. - As a service. This model enables the customer to provide trust services to its end-customers with minimum initial outlay. The business receives access to an API for QES services and becomes a Registration Authority (RA) for all subscribing customers. The financial institution remains in control of all valuable customer data and is the single point of contact to the customer.
This is the typical choice of banks which operate at a limited number of locations or wanting to focus on core competencies and end customer business.
Talk to us to discuss your most suitable infrastructure option.
References
- Selected articles on eIDAS (2014-today), by Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner, and more
- CEN/TC 224 - Trustworthy Systems Supporting Server Signing Part 2: Protection Profile for QSCD for Server Signing (05.2018), by AFNOR
- Conformity assessment of Trust Service Providers - Technical guidelines on trust services (2017), by the European Agency for Cyber Security
- Mutual Recognition Agreement of Information Technology Security Evaluation Certificates, VERSION 3.0 (Jan, 2010), SOG-IS
- Trustworthy Systems Supporting Server Signing Part 2: Protection
Profile for QSCD for Server Signing (2019) by CEN/TC 224 - About The Common Criteria (retrieved October 2020), by Common Criteria
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission