
An issuer is one of the corners in the ‘four corner’ model. An issuer is a financial organization (e.g. a bank) that produces payment cards and allows the cardholders to use them.
Issuers appear ‘twice’ in the four corner model. They ‘open’ it and they ‘close’ it.
Issuers, on one side, start the process by producing the payment cards and delivering them to the Cardholder and, on the other side, close the process by being the final destination of the authorization flow.
Safety of the issuer
At first glance, an issuer is better protected than a merchant or a cardholder but in reality, because the payment card actually belongs to the issuer, there are a lot of risks that the issuer must deal with, involving malevolent attempts to fake or clone payment cards. Often the security of the issuer is bound to the security of the cardholder but not always. It is the case, e.g., when the cardholder itself becomes rogue and poses a threat to the issuer.
Overview of the Issuer protection techniques in the payment industry
Cryptogram verification
EMV provides a cryptogram verification mechanism for issuers to check that a request for an online transaction is legitimate. The keys used for the cryptogram are shared between the payment card given to the cardholder and the issuer itself. When an online transaction request ‘hits’ the issuer, the cryptogram is verified. There are several types of cryptograms depending on the context but the principle is always the same.
Issuer Scripting
One of the most important security systems available for issuers to protect themselves is issuer scripting. This is generally a not well-known dispositif, but it can be very powerful.
The idea behind issuer scripting (or post-issuance scripting) is that the issuer is still able to control the payment card even after issuing and passing it to the cardholder. The payment card remains the eternal property of the issuer and it has the right to access it and modify it anytime.
To remotely access the payment card, the issuer uses a mechanism that is specified by EMVco and which allows it to send remote APDU commands (application protocol data unit) inside a secure channel (as specified by the Global Platform specifications) to the card, via an EMV payment terminal (ATM or EFT-POS terminal).
Issuer scripting is always processed by an EMV kernel. The kernel which is part of the payment terminal will receive the commands to send to the payment card and will ‘play’ them one by one. Because of the secure channel, the issuer authenticates itself to the card. Issuer Scripting is optionally sent after a successful online authentication via cryptograms.
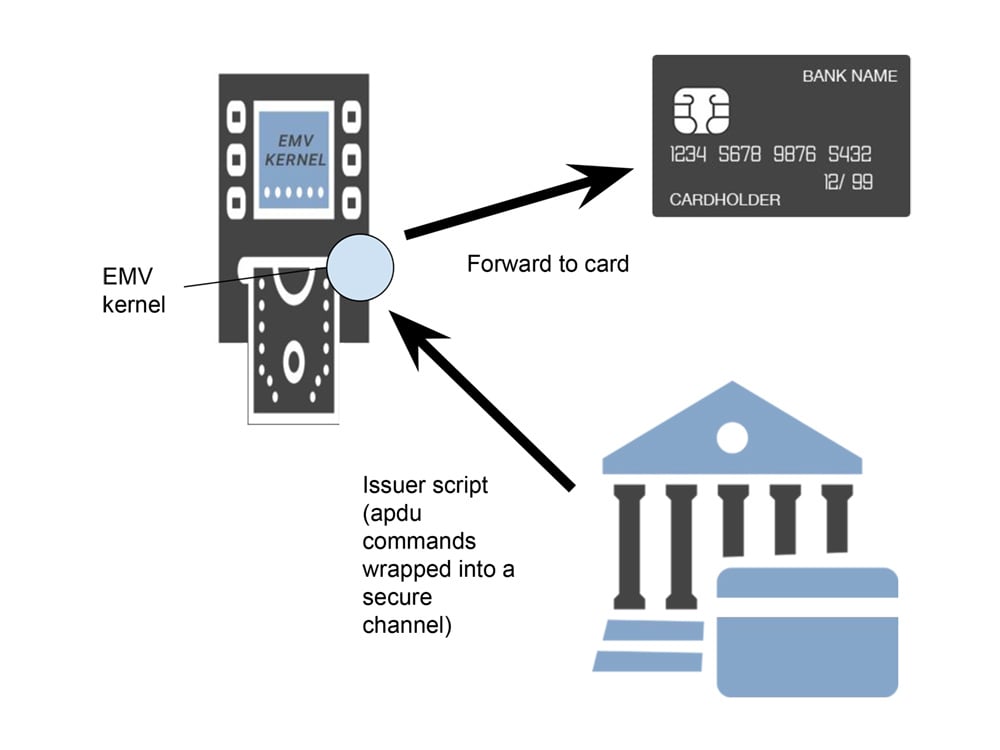
Any sort of supported commands may be sent, but usually the most common commands consist in changing the PIN of the card or blocking the card. In cases where a card has been misused (and that may involve malevolent usage by the cardholder itself as well), the issuer has the ability to block that card remotely as soon as it appears online from any of the EMV payment terminals connected to the EMV payment networks.
Anti-cloning
One of the biggest threats that the issuer faces is the cloning of an existing payment card. In the case of magnetic stripe, such cloning is quite trivial but by using EMV technology cloning of a card is technically close to impossible.
Anti-cloning technology is vital for the issuer. This involves secure chips which are tamper resistant, including resistance to side-channel attacks, such as differential power attacks (DPA). This may also involve using Physically Unclonable Functions (PUF). PUFs act like ‘biometric’ traits of machines and involve physical dependent signatures that cannot be replicated in the same way the hardware was created, because they involve complex and random mechanisms.
Protection of personalization systems
Issuing a card is a complex highly regulated process, where all the keys and specific parameters will be written into the card. Personalization must be extremely secure so that confidential and critical data cannot be intercepted or tampered. This is achieved by several levels of encryption, physical security in card personalization centers and usage of HSMs and Key Management Systems (KMS).
PKI system
EMV offers a PKI system that provides some security to the issuer. This PKI is part of the offline authentication and this involves the issuer dealing with a CA maintained by a card scheme.
The CA evaluates an initial certificate request (CSR) from the issuer and returns the issuer certificate (merely the public key of the issuer, signed by the CA). This issuer certificate will be used for DDA and CDA.
Conclusion
The issuers need to protect themselves from the misuse of their payment cards and from tampering of the confidential data that they process. This is achieved especially via a special mechanism known as issuer scripting. PCI DSS compliant hardware security modules and key management systems form the heart of the cryptographic infrastructure that protects the data required by the card personalization systems.
 Martin Rupp (guest)
Martin Rupp (guest)
