Cryptographic keys are used to secure data-at-rest and data-in-transit. Trying to keep them protected yet always available for use is one of the most difficult problems in practical cryptography. Improper key management can lead to key leakage, where an attacker obtains the key and recovers the sensitive messages from the encrypted data.
This article discusses the key management problems and Cryptomathic's approach to solving the challenges faced by large organizations that use cryptography for variety of applications.
Absence of central surveillance of the keys
In a traditional key management approach, when a key expires, key custodians are responsible manually updating these keys. Such activities create dependency on individuals and are more resource-intensive. This traditional approach to key management is inefficient and may create vulnerabilities, such as human error in updating system certificates or locating which systems to be updated. Ensuring that the right key is in the right place at the right time is mandated by many organizations.
Legacy applications or systems
Some applications, such as legacy applications, may also make it extremely difficult, if not impossible, to implement key management solutions. There are significant hidden costs to maintaining legacy hardware and software systems. The old adage "if it ain’t broke, don't fix it" may hold true for many things, but that may turn out to be a costly mistake for legacy systems.
These legacy applications were not designed with key management in mind. For instance, MD5, SHA-1 or DES may still be used for legacy applications, these algorithms should be replaced with more secure ones such as SHA-256, Whirlpool or 3DES. In the process of enabling or updating crypto on such systems, code level changes may be required. Most organizations prefer flexible application programming interfaces (APIs) that could easily handle the key management process without the need to rewrite most of the code.
Key life-cycle management and automation
Life-cycle management of a key is not restricted to generation and destruction alone but an end-to-end management of the key state from generation, backup, distribution, usage, expiry, revocation, update and destruction of keys. A key life-cycle state is one of a set of finite states that describe the current permitted conditions of a cryptographic key from key generation to destruction. A key management system (KMS) must provision the appropriate keys and deploy them to endpoints or the entities that use keys. Managing a large number of keys manually does not scale, suffers from human error, and is very expensive.
Instead of relying on tedious procedures for managing symmetric keys and asymmetric key pairs, a key management system, such as Cryptomathic’s Crypto Key Management System (CKMS), can facilitate easy management by providing the ability to automate and assign key attributes and current state details to each key. It includes encrypted keys to be sent or pushed from CKMS to any key distribution target as and when required.
Challenges in meeting regulatory compliance
Earlier, each application used to manage its own security policies and cryptographic keys. This can create lot of difficulties when trying to achieve or maintain regulatory compliance, such as PCI DSS or governmental regulation standards.
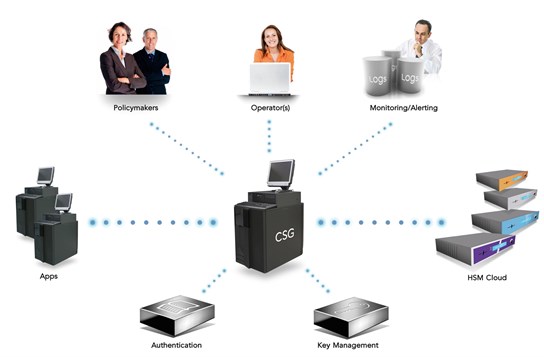
A proven solution to control such issues is the use of centralized policy management. The policy should define which type of algorithms can be used, which keys can be used, and a number of other attributes and parameters that are allowed for any given application. Cryptomathic’s Crypto Service Gateway (CSG) provides a centralized policy enforcement, where the system collects all relevant information in a single place for easy audit and is in human-readable form, so that demonstrating compliance with internal and external policies is much easier.
Development and testing
Testing applications for cryptographic functions is a cumbersome task. CSG reduces development time and cost for new projects as the solution uses a standard and common set of cryptographic functions that need not be tested for each new application demanding crypto services via CSG.
Cryptomathic's approach
Cryptomathic's advanced cryptography and key management products were developed to solve the above problems relating to the banking sector. This sector relies heavily on cryptography to securely provide services to its customers. With e-commerce technology expanding to more channels and presenting further business opportunities, organisations are striving to take advantage of the new services they can offer to their customers. Fundamentally, the security for all e-commerce is based around cryptography and the secure handling of the cryptographic keys. Having the right key management system in place enables a business to be agile in its services offering while maintaining control, flexibilty, scalablity, compliance and protection against attacks.