3 min read
Integrating PSD2 and eIDAS: Streamlining Compliance
Guillaume Forget & Jan Kjaersgaard : 21. June 2022

With the introduction of PSD2, banks are forced to provide third party payment service providers (PSPs) with access to the bank’s customers’ account information for account servicing and payment initiation services, but only in the case where the user has granted access to these third-party players. This article explores a technical solution that leverages eIDAS to address the PSD2 requirements.
In the terms of PSD2, before a bank can allow a PSP access to information about the user’s account, two conditions must be met:
- The PSP must authenticate towards the bank using an eIDAS PSD2 certificate and
- The user owning the account must have provided his/her consent for the PSP to access the account information
To meet these conditions, banks need a technical solution that can bridge the PSP to the authentication and signing scheme(s). This goes beyond the initial access to account (A2C) that banks initially focused on to ensure compliance against PSD2.
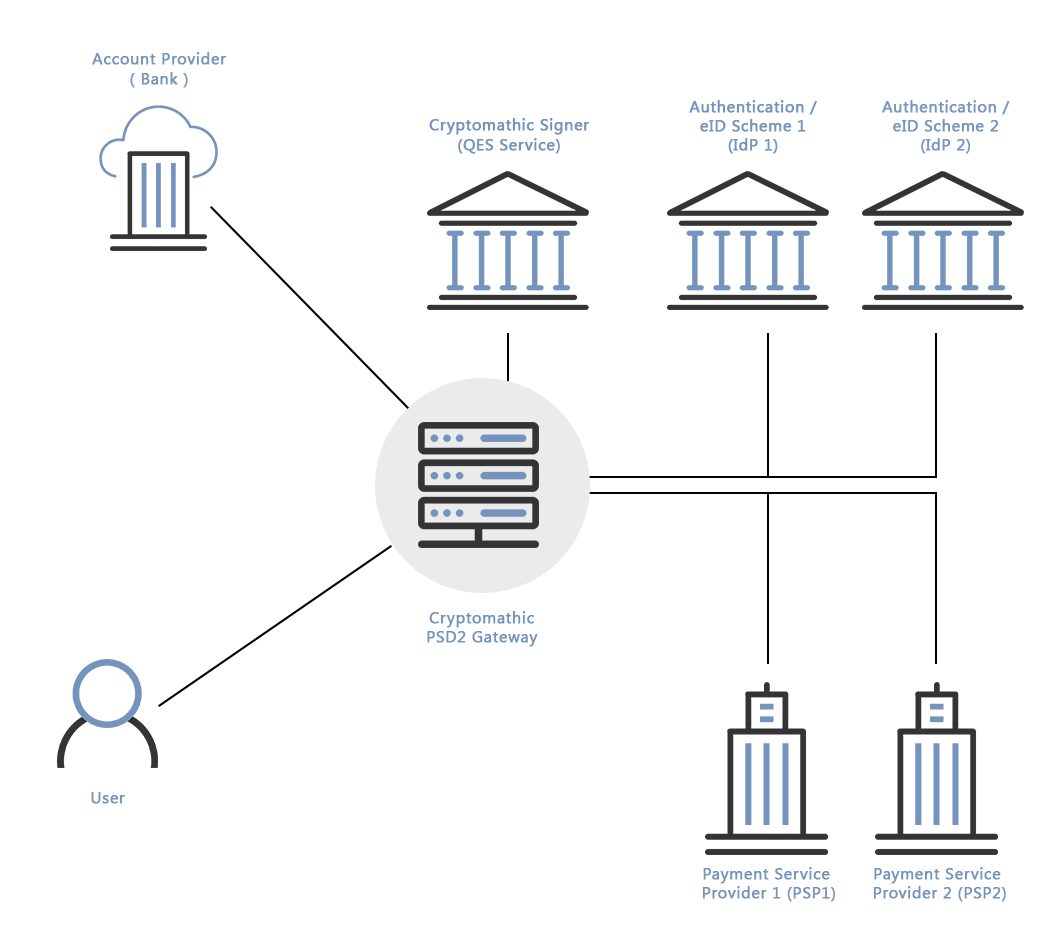
To this extent, Cryptomathic developed a PSD2 Gateway that brings together PSP and user authentication, user consent, transaction signing and access control into the banking environments (these topics where explored in [1] and [2]).
User authentication is conducted using internal or external authentication schemes. By using internal schemes, existing investment and deployments within the bank can perform the user authentication. Using external schemes, like the Nordic national identity schemes, allows for a well-known user experience. In both cases, following a successful authentication, the PSD2 Gateway is instructed to issue an OAuth Access Token, which may be used to access resources within the bank.
While PSD2 requires PSPs to use eIDAS certificates to authenticate towards the bank, this only covers a subset of the required trust services and does not solve the strong customer authentication (SCA) or user consent requirements. Integration with additional trust services is required to grant PSP applications and services access to different resources within the bank on behalf of the user. To achieve this, the PSD2 Gateway will issue an Access Token to be used by the service when accessing the resources.
eIDAS QES to ensure non-repudiable user consent
A Qualified Electronic Signature (QES) provided by a qualified trust service that is operated under the requirements from the eIDAS regulation delivers the highest level of assurance in terms security and liability. The trusted service operates under national state provision, where it is also held liable. The signature can be used by the user for signing user consent according to PSD2 as well as signing legally significant documents and transactions.
For a user to provide consent to grant a specific PSP to access his/her account information, the PSD2 Gateway uses existing signature schemes, like the Nordic national identity and signature schemes. Where the identity schemes do not provide an existing signing service, an internal service, provided by Cryptomathic Signer, can be used. In the latter case, the PSD2 Gateway acts as Signature Creation Application and provides Cryptomathic Signer with the SAML Assertion required to activate the signature key.
Cryptomathic Signer is a remote signature solution, certified as eIDAS QSCD, and can be used to let the user remotely sign transaction data and authorization requests. The input data can be formatted in XML or PDF and it supports delegated authentication, so that banks can leverage existing authentication components over SAML to ensure signature authorization.
Mobile security to achieve SCA on apps leveraging PSD2
Cryptomathic offers the Mobile App Security Core (MASC) framework, which is a security SDK designed for mobile app developers and comes with a set of security and protection functions to offer reverse engineering resistance, health monitoring, secure communication and storage. Cryptomathic MASC provides APIs to offer PSD2 compliant SCA with support for biometric authentication and challenge response protocols. It can also interact with existing IdP solutions.
References and Further Reading
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- Selected articles on Authentication (2014-today), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner and more
- eIDAS webinar 1: Using electronic Identification, Authentication and trust Services for Business (2018), by the European Commission
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission
- Proposal for a DIRECTIVE OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL amending Directive (EU) 2015/849 on the prevention of the use of the financial system for the purposes of money laundering or terrorist financing (2016), by the European Commission
- REGULATION (EU) 2016/679 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (2016), by the European Parliament and the European Council
-
Proposal for a REGULATION concerning the respect for private life and the protection of personal data in electronic communications and repealing Directive 2002/58/EC (Regulation on Privacy and Electronic Communications), (2017), by the European Parliament and the European Council
- Revised Directive 2015/2366 on Payment Services (commonly known as PSD2) (2015), by the European Parliament and the Council of the European Union
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
-
DIRECTIVE 2013/37/EU amending Directive 2003/98/EC on the re-use of public sector information (2013) by the European Parliament and the Council