
- Home >
- A Beginner’s Guide to PKCS #7 and Digital Signatures
In many parts of the world, including the European Union and the United States, businesses have adopted digital signing as a way to implement electronic signatures that are considered legally binding. This article introduces digital signatures, digital certificates, and the relationship between digital signatures and PKCS #7.
Digital Signature
A digital signature is proof of the authenticity of digital messages, files, executables, documents, etc. in modern communication by employing strong cryptographic techniques such as encryption and hashing. A unique digital ID (and a signing key) are required to create a digital signature. Digital IDs or certificates are based on asymmetric (or public key) cryptography, which uses key pairs (a combination of public and private keys). Public keys are openly distributed among the communicating entities, and the private (signing) keys are kept secret. The most common public key algorithm used is RSA.
Digital Certificate
A digital certificate is an electronic document used to prove ownership of a public key. The certificate includes the public key, information about its owner's identity and associated permissions.
Certificates provide the foundation for a PKI (public key infrastructure). Certificates are electronic representations of users, computers, network devices, or services. They are given out by a CA (Certificate Authority) and are linked to a pair of public and private keys. The current standard being used for digital certificates is X.509, as defined in RFC 5280. Some of the main parameters that exist in a certificate are:
- Certificate serial number
- Name of the certificate issuer
- Certificate issuer’s signature algorithm identifier
- Validity period
- Public key
Services provided by Digital Signature
A digital signature is basically a small block of data which is attached to the message to deliver the following security services:
-
 Sender/Source Authentication: A message/file is digitally signed by the private key of the sender and sent to the other party. The other party can only verify the signature from the sender’s public key, hence the authentication of the sender is achieved.
Sender/Source Authentication: A message/file is digitally signed by the private key of the sender and sent to the other party. The other party can only verify the signature from the sender’s public key, hence the authentication of the sender is achieved. - Message Integrity: Since the sender created the digital signature and no-one else can alter or modify during transit it so it means that message integrity is maintained.
- Non-Repudiation: Only the sender can create the digital signature which is verified by its public key, so the sender cannot deny the signature.
Process of Digital Signing and Verification
The process of digital signing and verification incorporates three steps:
- Key Generation: A key pair (private and public key) is generated by employing a public key algorithm such as RSA.
- Digital Signature Generation: Compute the cryptographic hash of the input file or message by using a secure hashing algorithm such as SHA-256, SHA-384, SHA-512 or Whirlpool etc. The computed hash is encrypted by the private key of sender resulting in the digital signature. The digital signature is sent along with the original file for its verification by the receiver.
- Digital Signature Verification: Sender computes the cryptographic hash of the received file or message by using the same hashing algorithm. Sender decrypts the digital signature by using the public key of the sender to get the hash sent by the sender. If the decrypted hash is exactly same as the computed hash of the received file, it means that digital signature is verified and data was not tampered with during transit.
Relationship between PKCS #7 Standard and Digital Signatures
PKCS #7 named as “Cryptographic Message Syntax Standard” is one the most famous and extensively used standard from the series of PKCS (Public Key Cryptography Standards) by RSA Security LLC. PKCS #7 is the specific standard used for generation and verification of digital signatures and certificates managed by a PKI (Public Key Infrastructure). This standard served as the basis for the S/MIME (Secure/Multipurpose Internet Mail Extensions) standard. PKCS #7 proposes a broad-spectrum syntax and format for creation of digital signatures which is elaborated in detail in RFC 2315. It also allows compatibility with Privacy-Enhanced Mail (PEM) format which is the default and most commonly used file format for storage and sharing of crypto keys and digital certificates. PKCS #7 allows PEM compatible signed-data to be converted into PEM messages.
When using PKCS #7, the result is the exportation of one type “ContentInfo”, in addition to the various object identifiers that are produced. Within this method, there are six general content types:
- Data
- Signed Data
- Enveloped Data
- Signed-and-enveloped data
- Digested data
- Encrypted data
These types are classified into two classes:
- Base: contains content types with no cryptographic enhancements. This is used only for the data content type.
- Enhanced: contains content types that contain encrypted data or other cryptographic enhancements. The remaining five types fall under this class.
The content types that fall under the enhanced class use encapsulation to encrypt data. These types are prepared with a single pass through indefinite-length BER encoding and are subsequently processed in a single pass using any BER encoding. This is useful when processing data from other processes. A sample S/MIME digital signature created by the private key is shown in the following figure:
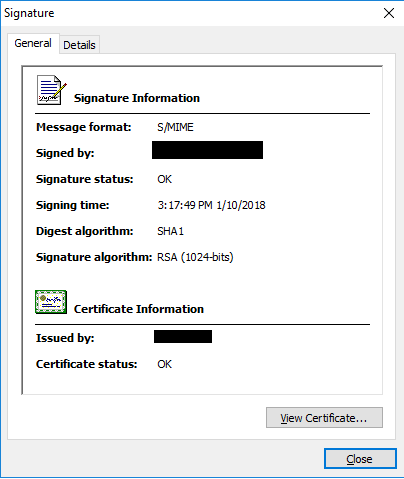
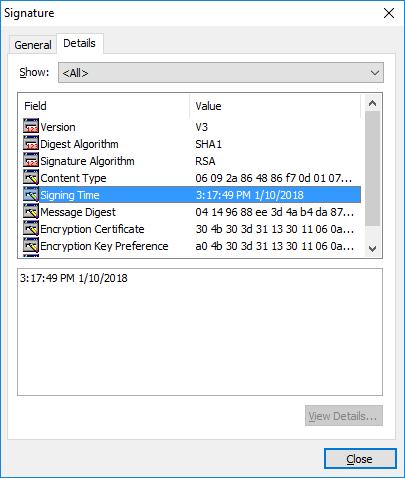
More details of the signature such as version digest algorithm, signature algorithm, content type, signing time and encryption certificate are shown in the following figure:
Conclusion
We have seen how there is a comprehensive set of standards and techniques that mean digital signatures have a very well established framework. Building upon this, regulations such as eIDAS (in the EU) and UETA and E-SIGN ( in the USA) raise the game further by allowing digital signatures entirely equal legal status to traditional “wet” signatures. Specialist security companies, like Cryptomathic, have a strong track record of deploying very dependable, large-scale remote digital signature solutions that fulfill all the strict criteria of the regulations (with eIDAS being the most comprehensive and stringent).
References
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Asim Mehmood, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- Selected articles on Authentication (2014-today), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner, and more
- Selected articles on eIDAS (2014-17), by Heather Walker, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner and more
PKCS #7: Cryptographic Message Syntax Version 1.5 (1998), by B.Kaliski, RSA Laboratories
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC(2014) by the European Parliament and the European Commission
-
Electronic Signatures and Infrastructures Activities (2017), by ETSI
- Electronic Signatures in Gobal and National Commerce Act(2000), US-Government
-
Uniform Electronic Transactions Act (2000), as an example the publication by the State of Virginia
