
- Home >
- Issuing MULTOS Cards: Emerging Security Technology
MULTOS cards are being deployed in steadily increasing numbers and Cryptomathic is delighted to be involved in MULTOS projects across the globe.
MULTOS is a high-security card platform and issuing model in which the "personalization" of cards with the cardholders' data is done in one single logical step before reaching the actual personalization machines. This is quite the opposite to the standard method of personalizing native cards where the data is sent to the cards, element by element and thereby increasing a potential exposure of sensitive data.
Cryptomathic supports MULTOS issuing through CardInk - a data preparation system for EMV and magnetic stripe cards - which has recently been expanded with a range of applications supporting the MULTOS platform. We offer, amongst other applications, MasterCard, Visa and SPAN2. SPAN2 is used in the Kingdom of Saudi Arabia on multi application cards that contain a second Visa or MasterCard application for international use.
Contactless - The New Emerging Technology
The latest technology advancement within the field of payment cards is the so-called contactless card. With a contactless card one does not have to insert the card into a reader when paying - it is sufficient to place the card within the proximity of the reader, say 10cm, and the transaction will take place "through the air". The purpose of contactless cards is to enable ease and speed of use, particularly for low value transactions. Cryptomathic is in the process of finalising a MULTOS implementation on MasterCard contactless cards (MICA / MACU) with a planned release shortly before Christmas.
Security in a Complex Environment
In an attempt to explain the increased interest in MULTOS one could consider the dynamics of card prices, intensified sales and marketing efforts (especially from MasterCard), and the industry recognition of the relatively high level of security involved. MULTOS has traditionally been associated with MasterCard but the model has proven flexible enough to now support other players in the market.
 Needless to say the use of such a complex model means added requirements regarding both functionality and security. A lot of players are involved when a bank decides to engage in a MULTOS project, and because the technology is still evolving, constant attention to industry requirements, practices and technology is necessary.
Needless to say the use of such a complex model means added requirements regarding both functionality and security. A lot of players are involved when a bank decides to engage in a MULTOS project, and because the technology is still evolving, constant attention to industry requirements, practices and technology is necessary.
MULTOS applications are required to integrate with other payment scheme specific software products / instances, and necessitate bit-by-bit precision formatting of the so-called Application Load Units (ALUs) that are used to personalize the cards. This last part is particularly non-trivial as each card type and each application has its own requirements and formats, thus we have made substantial investments to implement the management of this into CardInk.
The security requirements are also more comprehensive than for native card issuing. Examples include the generation and management of more DES and RSA cryptographic keys, securing personal data using both symmetric and asymmetric encryption, and digital signatures. Specialising in commercial cryptography, it has been interesting for us to enter this area and we are happy to admit that we have had to make full use of our skills to accomplish the implementations.
Image 1: Structure of an Application Load Unit
Image 2: The KTU-Prime Method
Image 3: Optimised MULTOS Production Model
Loading Applications
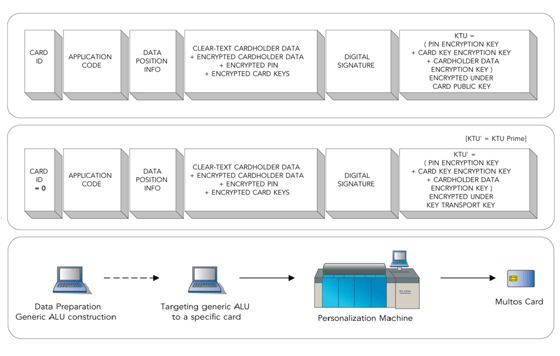
The data preparation system receives the actual application that will run on the card from an external supplier; in principle simply a software application that will be loaded and run on the MULTOS card operating system. This application manages the interaction with an ATM or pointof- sale terminal based on data received from the bank host or card management system containing a list of cardholder names, account numbers, spending limits etc. The data preparation system maps the data to specific data addresses. For particularly sensitive data a sequence of encryption keys are generated and used to encrypt the individual data segments. These encryption keys are collected and placed in a Key Transformation Unit (KTU), and further encrypted under yet another key. Lastly the data is signed by a digital signature. Together these combined data components form the Application Load Unit.
When the ALU is loaded onto the card, the card verifies the digital signature, and decrypts the sensitive data. To accomplish this, the data preparation system and the card must previously have exchanged information about the signature keys / certificates, encryption keys, application layout, and go through key management authorities - just to mention some of the interface points.
In the basic MULTOS scheme the KTU is directly RSA-encrypted using a key specific for each card. Thereby each file produced corresponds to a specific card. In practice however, this has proven unfortunate as some cards do fail during production leading back to a second round of data preparation with a new card ID, new keys etc., all of which can be cumbersome.
To address this issue MULTOS has introduced an intermediate step model where one generates the data for a generic card and uses only symmetric encryption of the KTU. At production, the card ID is then read from the card and the ALU is re-encrypted to target the specific card Optimized Multos production model with the card's RSA public key. This way a failed card can be immediately replaced. This new method is called the KTU-Prime Method.
Extended Key Management
CardInk contains complete key management functionality for MULTOS, in addition to card issuing. However, for customers with a large amount of cryptographic keys to manage we also offer a specific product, the Cryptomathic Key Management System (CKMS). All the cryptographic keys can be managed in CMKS and be pushed to CardInk to enable separation of operations and avoid key management ceremonies in the production environment.
 MULTOS step/one - A Variant Application
MULTOS step/one - A Variant Application
An alternative offering within the MULTOS framework is the MULTOS step/one card. The step/one application is structured around the same principles as conventional MULTOS cards, but it excludes RSA cryptography for both the actual payment application and the method of constructing the ALU. The payment application is an SDA (Static Data Authentication) application - the card security is based on a pre-calculated digital signature on the card data, as opposed to a DDA (Dynamic Data Authentication) application where each card has its own RSA key pair. For the ALU construction the digital signature is made using a DES MAC and the contained cryptographic keys are likewise DES encrypted. The advantages of a MULTOS step/one card is its simpler application and implementation, which further results in lower card prices.
Previously published in Cryptomathic NewsOnInk, 2007
Image: "Rainbow of credit cards", courtesy of frankieleon, Flickr (CC BY 2.0)