
Today’s cars are computers on wheels which operate in a connected world and ecosystem of other cars, roadside infrastructure, and the cloud. Car drivers can unlock their cars with wireless key-fobs or phones, retrieve updates of their cars main software over-the-air (OTA), or have issues diagnosed remotely. Soon they will pay for goods and services at the gas station or electronic vehicle charging station.
Whence, cybersecurity and software update management in the automotive space are becoming as important for the safety and security of a software-defined vehicle as the physical brakes and qualified tune-ups for a traditional car. This is also reflected by the 2020 UNECE Regulations No. 155 and No. 156: UNECE R155, to be viewed in conjunction with the guidelines provided by ISO/SAE 21424, requires a Cybersecurity Management System (CSMS) for new connected or automated vehicles. Meanwhile, UNECE R156, to be viewed in conjunction with ISO 24089, postulates a Software Update Management System (SUMS). Correspondingly, to achieve compliance with UNECE R155 and R156, vehicle manufactures must have clearly defined risk management for cyber threats as well as sound processes for secure software distribution and secure software updates that comply with the specifications.
Identified threats include threats to the vehicle communication channels, threats to the software update process, threats relating to unintended human actions, threats to external connectivity and connections, or threats related to data loss or data breach from vehicle. Some mechanisms to mitigate these threats are data encryption, device and vehicle authentication, code signing, and access control techniques. To implement such measures, a variety of cryptographic algorithms are needed, in which cryptographic keys play a fundamental role.
In the following, we outline a few use cases for cryptographic keys in the automotive space.
Needs and Solutions
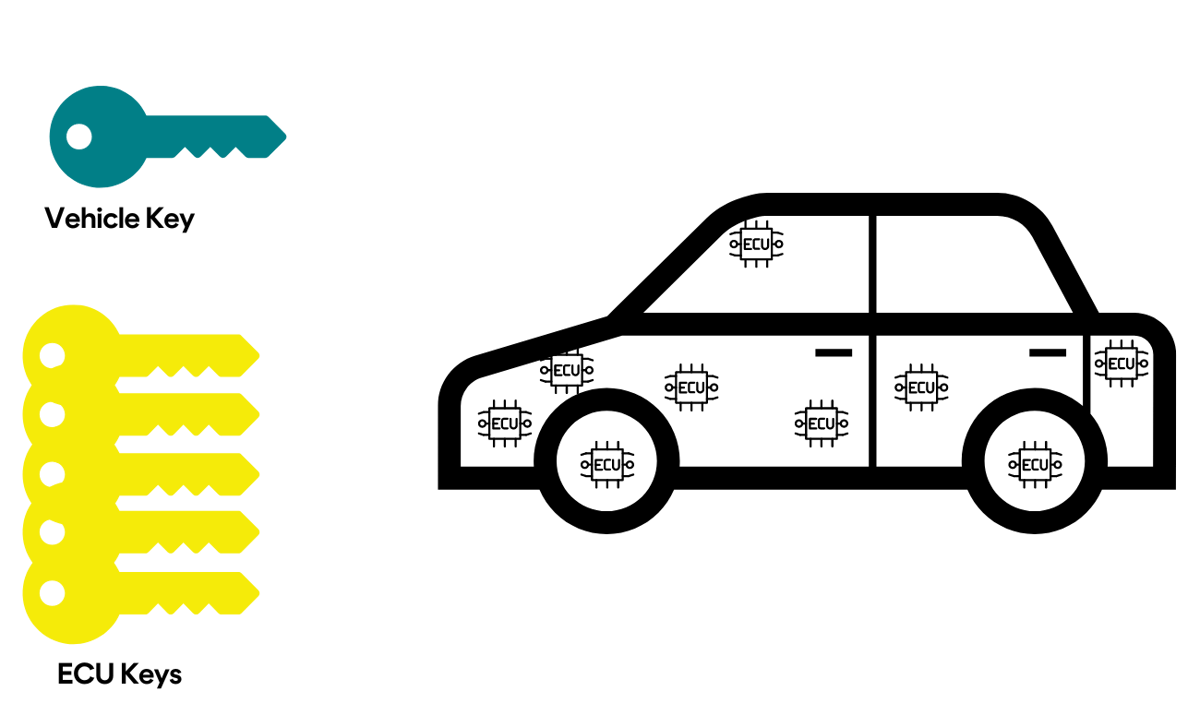
From production to day-to-day driving and maintenance, cryptographic key management is essential to guarantee the necessary level of security of the automotive ecosystem, ensuring that the correct keys are in the right place at the right time. Whether it’s towards secure vehicle production and installation of the 100 or more electronic control units (ECUs) in a car, firmware over-the-air (FOTA) updates, or electronic periodic technical inspection (ePTI), a significant number of cryptographic keys are required, both symmetric keys and asymmetric key pairs. In the face of increasingly connected cars and an increasing number of ECUs that need monitoring and updating, exponential growth of the number of those keys is foreseeable.
The table below shows some of those keys.
|
Use Case |
Key |
Type |
Location of Use |
Purpose |
|
Secure Production |
Vehicle key |
Symmetric |
Vehicle & ECUs |
Authentication |
|
Secure Production |
ECU key |
Symmetric |
ECU |
Authentication |
|
FOTA |
Supplier key pair |
Asymmetric |
Manufacturer |
Code-Signing |
|
FOTA |
Supplier Certificate |
|
Supplier & ECU |
Authentication |
|
FOTA |
Supplier key |
Symmetric |
Manufacturer & ECU |
Confidentiality (IP Protection) |
|
ePTI |
ePTI provider certificate (short-lived) |
|
ePTI Provider & ECU |
Authentication & Access Control |
Secure Vehicle Assembly & ID Injection
Secure vehicle production requires vehicle and ECU identities to be securely issued and securely managed. Typically, ECUs come from the supplier-side with their own identities, e.g., in the form of symmetric keys to be used in a Message Authentication Code (MAC) function, which upon vehicle assembly should be updated to place them under the manufacturer’s control. Similarly, a symmetric (MAC) key that is unique to each vehicle should be placed in all vehicle’s ECUs at vehicle assembly. Both serve to authenticate all communications among a vehicle’s ECU, as well as with the backend, thereby preventing a malicious actor from manipulating the vehicle’s system. All keys must be managed, and secured, throughout the ECUs’ and the vehicle’s life spans.
%20v1.png?width=1200&length=1200&name=KMS%20%20PKI%20diagram%20for%20automotive%20blog%20(1083%20x%20750%20px)%20v1.png)
Secure FOTA (Firmware over-the-Air) Updates
ECUs periodically need firmware updates which preferably happen without the need for physical access to the vehicle. The method of choice is an over-the-air update, e.g., via a cellular or Wi-Fi connection which however comes with the risk of a malicious actor distributing harmful software. It therefore is crucial to ensure authenticity and integrity of the update, which requires authentication and code-signing of the update before its transmission to the vehicle. Upon receiving an FOTA update, the vehicle needs to verify the digital signature that is used to sign the update. If in addition a supplier’s intellectual property (IP) is to be protected, the update also needs to be encrypted before transmission to the ECU and decrypted by the ECU upon receipt.
A key management system (KMS) at the manufacturer’s backend along with a public key infrastructure (PKI) integration can assist with all of that.
Electronic Periodical Technical Inspection (ePTI)
Vehicle systems must undergo a variety of diagnostic services at predefined intervals by authorized providers. Such periodical technical inspections (PTIs) are crucial to ensure that a vehicle is in a safe and environmentally acceptable condition during its use. Vehicle systems that consist of one or multiple ECUs with dedicated sensors and actuators are classified as ePTI-relevant systems and require electronic PTIs (ePTIs) -- with technical and communication requirements detailed in ISO 20730-1, ISO 20730-2, and ISO 20730-3. For a vehicle to grant an ePTI provider’s test equipment access to specific ePTI-relevant systems, a proper authentication and authorization mechanism is of uttermost importance. This can be facilitated by means of short-lived certificates.
A KMS at the manufacturer’s back end along with a PKI integration can assist with that.
Crypto Agility Is a Must
Crypto agility is a system’s capability of seamlessly changing cryptographic parameters or algorithms. This feature is particularly important given the threat of quantum computing: Within the next 10 or so years, a quantum computer may be built that is powerful enough to break all asymmetric cryptographic algorithms currently in use (RSA, Elliptic Curve-based Cryptosystems) and reduce the security of symmetric crypto algorithm (such as AES). Alongside, standards are being written that making the use of quantum-computing resistant asymmetric algorithms mandatory.
Given an expected life span of more than 10 years for a vehicle, a KMS being deployed today in the automotive world must be able to deploy quantum-computing resistant cryptography in the future, as the need arises or as soon as the other players in the field (such as ECUs) are ready for this.
CrystalKey 360
CrystalKey 360 is Cryptomathic’s key management and data security platform, which provides crypto agile key management and Crypto-as-a-Service (CaaS). With CrystalKey 360 you can take control and achieve compliance by consolidating the management of all your keys and ensuring that keys are used according to company policies and industry best practices.
CrystalKey 360 provides:
- Centralized and automated key life-cycle management.
- Automated key distribution and exchange of keys in a variety of formats.
- Application tailored crypto agile services with centralized control of key access and associated cryptographic algorithms.
- Consolidated, streamlined, vendor agnostic HSM-as-a-service for your entire business.
- Tamper evident audit and usage logs for all keys and cryptographic operations.
CrystalKey 360 provides fully fledged APIs for key management and crypto service-related activities for supporting interoperability with homegrown and 3rd party systems, empowering businesses to effortlessly integrate key management into their organization. This among others enables businesses to seamlessly integrate CrystalKey 360 with existing Certificate Authorities (CA) or Certificate Life-cycle Management (CLM) systems providing full PKI support and integration into existing infrastructures.
A well-designed key management system such as CrystalKey 360 that offers security by design along with comprehensive logging can help vehicle manufacturers be compliant with the cyber security and software update management requirements as specified in UNECE R155 and UNECE R156.
Complete the form below to discover how Cryptomathic can help your business achieve security by design:
 Edlyn Teske
Edlyn Teske