2 min read
The European Digital Identity Wallet as a Means of Authentication
 Edlyn Teske
:
28. June 2023
Edlyn Teske
:
28. June 2023

- Home >
- The European Digital Identity Wallet as a Means of Authentication
The European Commission, as part of the eIDAS 2.0 proposal promotes the European Digital Identity Wallet (EUDI Wallet) as an app that enables citizens and residents all over the EU to identify and authenticate themselves. EUDI Wallet users should also be able to store and selectively disclose, locally and remotely, digital travel credentials (ePassports), driver’s licenses, university diplomas, as well as personal information including medical records or bank account details. The wallet should also allow its users to access a variety of online services, and sign documents with qualified electronic signatures and seals (QES). The scope of this wallet app is described in some detail in The Common Union Toolbox for a Coordinated Approach Towards a European Digital Identity Framework, and a reference implementation is expected for September 2023.
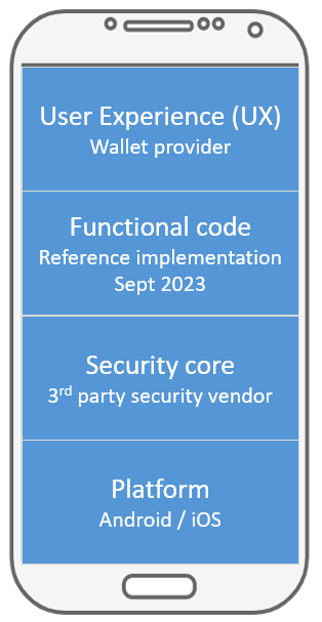
Given the high value of the digital assets stored in the wallet and the huge amount of material and reputational damage that could result from any vulnerability, it is understood that the EUDI wallet must offer a high level of protection against a variety of attacks, including attacks from adjacent malware that may have been installed by naïve users, or professional and dedicated attacks on an emulated or rooted platform.
The EUDI reference implementation anticipated for September 2023 may include an embedded crypto interface and interfaces to a TEE and native SE. Such tamper-resistant hardware is vital for the security of the EUDI Wallet to provide additional runtime protection and key storage, rollback prevention, device binding, and (true) random number generation.
Most modern mobile devices have a TEE/SE in one form or another. In fact, it is well possible for a hardware-defined secure environment to be enforced by the OS provider!
As a dedicated secure subsystem, Apple’s Secure Enclave Processor is part of their mobile devices since iPhone 5s. Meanwhile, a TEE is mandatory on devices launched with Android 8 Oreo and higher, and with Android 9 Pie, Google introduced StrongBox. Both the Secure Enclave and StrongBox contain CPUs separate from the rest of the device and provide dedicated hardware-backed storage of (decryption) keys and biometric data, as well as a true random number generator.
Such features look good on paper, but a high-risk asset such as the EUDI wallet needs security-certified software and hardware. Specifically, it is stated in Article 1 (7) 4 (c) of the eIDAS 2.0 proposal that Digital Identity Wallets shall “meet the requirements set out in Article 8 [of Regulation (EU) No 910/2014] with regards to assurance level ‘high’, in particular as applied to the requirements for identity proofing and verification, and electronic identification means management and authentication”. While the EUDI wallet may not take an active role in identity proofing and verification as these services can be achieved using existing frameworks, it will most likely be used as an authentication means.
What is needed to meet those requirements with regards to assurance level ‘high’ is found in Section 2.2.1 of the Commission Implementing Regulation (EU) 2015/1502 on setting out minimum technical specifications and procedures for electronic identification means pursuant to Article 8(3) of Regulation (EU) No 910/2014 of the European Parliament and of the Council. Namely, that
- The electronic identification means utilizes at least two authentication factors from different categories;
- The electronic identification means is designed so that it can be assumed to be used only if under the control or possession of the person to whom it belongs;
- The electronic identification means protects against duplication and tampering as well as against attackers with high attack potential; and
- The electronic identification means is designed so that it can be reliably protected by the person to whom it belongs against use by others.
There are already several mobile app based eIDs notified to the EU commission at assurance level substantial and even high. Such solutions to demonstrate conformance with the eIDAS regulation leverage on using third party libraries (such as the Cryptomathic Mobile Application Security Core) to address the plethora of current and evolving threats related to the EUDI wallet. But also the best-practice software security core leverages on available security mechanism and takes advantage of complementing hardware security features provided by Trusted Execution Environments (TEE) or Secure Elements (SE).