5 min read
Overview of the NIST Digital Identity Model compared to eIDAS
Cryptomathic : 19. July 2018

- Home >
- Overview of the NIST Digital Identity Model compared to eIDAS
To combat fraud in digital identities and provide guidelines for digital authentication, the National Institute of Standards and Technology (NIST) updated its Digital Identity Guidelines in June 2017 and has provided a digital identity model that represents their updated guidelines with technologies and architectures that are currently available. This article describes the NIST model and compares NIST’s US-minded approach with the European eIDAS-Regulation and its legal framework.
When engaged in an online transaction, a digital identity represents the individual who is attempting to access the digital service. When used to access a digital service, the individual’s real-life identity might not be known. However, through the use of identity proofing, it can be established that the individuals are who they say they are.
This is where digital authentication is used to determine the validity of one or more authentication mechanisms (or "authenticators") that will provide evidence of the individual’s identity.
The NIST digital identity model represents what goes on behind the scenes, as a digital identity is authenticated before access is granted to a particular digital service.
Terminologies Used in the Digital Identity Model
There are numerous terms that are used in the Digital Identity model that relate to the involved entities and the various functions that occur in this model.
- Identity Assurance Level (IAL) addresses the identity proofing process and includes:
- Verifier is the party that verifies the claimant’s identity.
- Claimant is the party to be authenticated.
- Subscriber is an applicant that has successfully completed the proofing process.
- Applicant is the party to be proofed.
- Identity Proofing is the process of verifying the subject’s association with his or her real world identity.
- Relying Parties (RPs) depends on the CSP and the verifier to assert information about the subscriber.
- Registration Authority (RA) and Identity Manager (IM) may perform some of the duties of a CSP.
- Credential Service Providers (CSPs) perform certain enrollment, identity proofing and issuance processes.
- IAL1 where no link to a specific real-life identity is required.
- IAL2 where evidence is available to prove and verify the real-world existence of the claimed identity.
- IAL3 where a physical presence is required for identity proofing.
- Authenticator Assurance Level (AAL) refers to process of authentication and also has three subsets:
- AAL1 gives a low assurance that the claimant has control of an authenticator that is bound to the subscriber account, using single or multi-factor authentication technologies.
- AAL2 provides a high assurance that the claimant has control of the authenticators that are bound to a subscriber’s account. Secure authentication protocol(s) for proof and control of two authentication factors, including approved cryptographic processes are required.
- AAL3 provides very high assurance that a claimant is in control of the authenticator(s) that are bound to the subscribing account. This level requires the proof of possession of a cryptographic key and the use of a hardware-based cryptographic authenticator that also resists verifier impersonation.
- Federation Assurance Level (FAL) is the assertion protocol that is used in a federated environment that communicates authentication information to the RP.
Behind the Scenes of the Digital Identity Model
The Digital Identity Model tracks the enrollment, credential issuance, lifecycle management activities and various processes that occur during the identity proofing and authentication procedure.
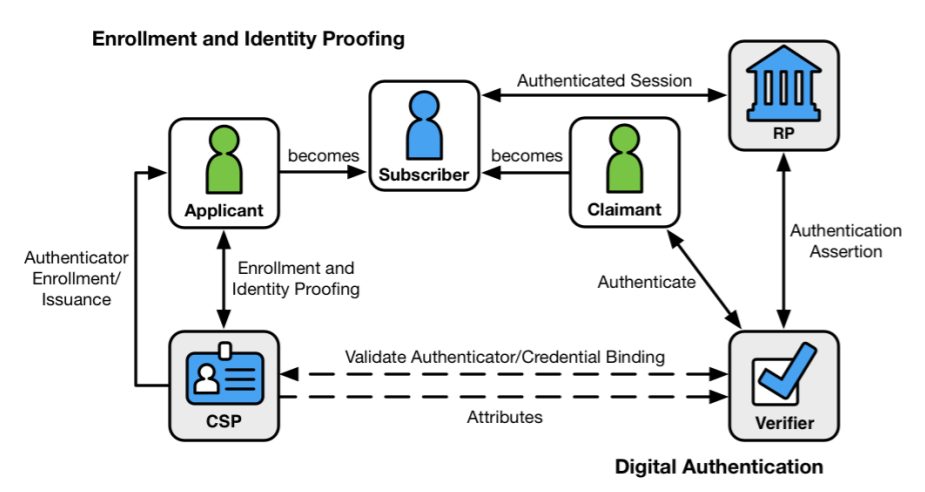
Figure: NIST Digital Identity Model, Source: NIST Special Publication 800-63 Volume 3 Revision 3, Digital Identity Guidelines
These interactions generally occur in the following sequences:
Identity Proofing
- The applicant applies to the CSP to begin the enrollment and identity proofing processes.
- The CSP performs identity proofing on the applicant. If the proofing is successful, the applicant will be elevated to the level of a subscriber.
- The CSP and the subscriber will then establish authenticator(s) and a corresponding credential.
- The CSP will then maintain the credential, its status and the collected enrollment data at a minimum for the lifespan of the credential. Meanwhile, the subscriber will maintain their authenticator(s).
Authentication
- The subscriber will be referred to as a claimant as they use an authentication protocol to prove possession and control of their authenticator(s).
- The verifier will interact with the CSP to validate a credential that will bind the subscriber’s identity to their authenticator(s) and to obtain claimant attributes where needed.
- The CSP or verifier gives the RP an assertion about the subscriber. The RP will use that information to determine whether to authorize access to the subscriber.
- If an authorization is granted, an authenticated session will be established between the RP and the subscriber.
NIST Special Publication 800-63 Volume 3, Digital Identity Guidelines delves further into the updated Digital Identity processes.
NIST 800-63 and eIDAS
The general processes of enrollment and identity proofing in NIST 800-63 and eIDAS have the ISO 29003 standard as the common denominator. The National Institute of Standards and Technology suggests an informative mapping of the Identity Assurance Levels (IAL) and the Authenticator Assurance Levels (AAL) of the NIST standard and those defined under the European Union’s eIDAS Regulation, allowing for international identity federation and interoperability.
| NIST SP 800-53 | eIDAS |
| AAL / IAL 1 | Low |
| AAL / IAL 2 | Substantial |
| AAL / IAL 3 | High |
The basic differences are not necessarily in the procedures, but in the legal standing and in its entourage of accompanying standards.
The DocuSign Case and eIDAS' probative value
The DocuSign case in 2016 made a significant point when the U.S. Bankruptcy court in California ruled that in the USA, electronic signatures, as used in the DocuSign software, do not constitute as a replacement for original signatures on legal documents and the like.
In contrast to the US case, the eIDAS regulation enforces the standards and procedures, which enable electronic signatures to have the same probative value as a handwritten signature - the highest level of security and probative value for a digital signature is called a Qualified Electronic Signature (QES). A QES can be used on legal documents as well as evidence in a court of law. This means a person gets full legal capacity to act through his/her digital identity.
Instead of a CSP, eIDAS uses a more overarching term "Trust Service Provider" (TSP). To provide qualified trust services, including digital identity verification and digital signing, the TSP needs to be achieve qualified status and certified as a Qualified TSP (QTSP) by the supervisory body in its Member nation. A QTSP must follow the strict standards provided under the European eIDAS Regulation, where the supervisory body will ensure compliance with these standards.
Not just signatures - the Single Digital Market around eIDAS
The eIDAS regulation is in force for all member states of the European Union, allowing for cross-border interoperability. It is supported by a whole suite of standards developed by the European Telecommunications Standards Institute. These standards include technical specifications for digital signatures, e.g. XAdES, PAdES, CAdES.
In the pursuit of creating a secure, comfortable, barrier-free digital single market, the EU expands this set of standards by a concisely defined digital service infrastructure, covering essential components like user identification and authentication, communication, invoicing, payment and electronic service delivery, enlarging the citizens' capacity to act even further based on eIDAS.
Looking Forward
For now the NIST Digital Identity Model is lacking its legal structure and the ecosystem surrounding standards. For the NIST Identity Model to reach its full potential requires a legal framework to support it, as well as some procedural framework (including eDelivery and eInvoicing).
The NIST 800-63 and eIDAS have enough similarities so that the often-claimed multilateralism could easily gain new pace through seamless US-EU cross-border business. Both sides would win. It just needs more than a standard on the US-side - it needs the legal framework.
References
- NIST Special Publication 800-63-3: Digital Identity Guidelines (07/2017), by Paul A. Grassi, Michael E. Garcia and James L. Fenton, the National Institute of Standards and Technology
- Selected articles on Authentication (2014-18), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner and more
- Selected articles on Electronic Signing and Digital Signatures (2014-todays), by Ashiq JA, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, Tricia Wittig and more
- Proposal for a DIRECTIVE OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL amending Directive (EU) 2015/849 on the prevention of the use of the financial system for the purposes of money laundering or terrorist financing (2016), by the European Commission
-
Proposal for a REGULATION concerning the respect for private life and the protection of personal data in electronic communications and repealing Directive 2002/58/EC (Regulation on Privacy and Electronic Communications), (2017), by the European Parliament and the European Council
- Revised Directive 2015/2366 on Payment Services (commonly known as PSD2) (2015), by the European Parliament and the Council of the European Union
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
- DIRECTIVE 2013/37/EU amending Directive 2003/98/EC on the re-use of public sector information (2013) by the European Parliament and the Council
Image: Digital Art, courtesy of Rishbh Sharma, Flickr (CC BY 2.0)
