2 min read
Payment Security and Key Blocks: Why are key blocks so secure?
 Martin Rupp (guest)
:
18. June 2021
Martin Rupp (guest)
:
18. June 2021

How can keys be securely exchanged over potentially unprotected channels? The answer to this question is “key blocks”. A key block is an essential cryptographic key format that allows users to securely exchange and utilize keys over various environments.
Merely encrypting a key with a key encryption key (KEK) is not sufficient as there are potentially several unknowns, e.g.:
- What does the ciphered key represent ?
- What is the ID of the key which has been ciphered and has been transmitted?
- How should it be used, and so on...
If such information is missing, the key cannot be used in a system where there is more than one cryptographic key. If we add the information in plaintext, then the key can be tampered with over the potentially unprotected channel. This creates a security risk, such as a denial-of-service (DoS) attack or other attempts to attack the system. If the information is ciphered together with the key, this means only the users who have the deciphering key can know what the key must be used for. However, in a complex, secure, and distributed cryptographic system, this is not really convenient.
Another issue to consider is that any stream of bytes, malformed but respecting a certain padding, can be sent to the system and be misinterpreted by the system and cause hazardous outcomes.
Key blocks were created to protect cryptographic systems and mitigate against the above vulnerabilities.
Key Block Security
Key blocks follow a specific structure to keep data secure. They must protect the system that receives the protected keys from differential cryptographic attacks.
Key blocks must prevent the interception of the data by a malevolent middleman and the rearranging of the ciphered key component(s). This is very simply and efficiently done by using the authentication part (the MAC part).
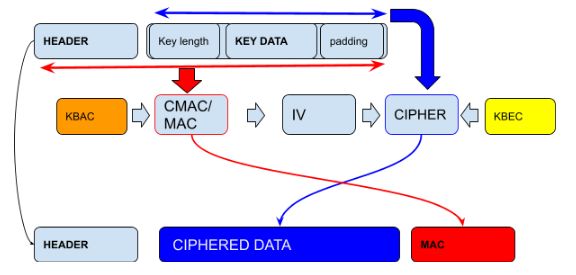
KBEC and KBAC
In a standard key block, there are two encryption keys. One, the key block encryption key (KBEC), used to cipher the key component . The other is the key block authentication key (KBAC), used for computing the MAC part, over the header + unciphered key part.
Here is a standard representation of what the two keys achieve:
These two keys are usually derived from a single master key.
Analysis of the Security
Obviously, the key block is only as secure as the encryption algorithm and the MAC algorithm that is used for it. If an attacker can form collisions or use tables (such as rainbow tables) to break the MAC, then the security of the key block will be weak.
Additionally, both the KBAC and KBEC keys must have good entropy. Ideally, they must be generated by a process that provides ‘almost’ 8 bits of (Shannon) entropy.
If the padding used by the cipher has a known vulnerability, CBC for instance, then this will impact the security of the key blocks scheme.
Typically, if all security constraints are respected, the key block will provide excellent security and will be capable of resisting known attacks.
While the concept is pretty straightforward, key blocks have been found to significantly enhance the protection of cryptographic keys - beyond merely using key encryption keys for distribution. If correctly implemented, they will ensure the confidentiality and integrity of a key during its transfer via potentially insecure channels.
References and Further Reading
- More articles on Key Blocks (2019 - today), by Dawn M. Turner and Martin Rupp
- More articles on Key Management (2015 - today), by Matt & Peter Landrock, Stefan Hansen, Dawn Turner, and more
- Information Supplement: PIN Security Requirement 18-3 - Key Blocks (2019), by the PCI Security Standards Council