Securing Mobile Banking Apps with MASC
Understand the threat landscape and how MASC's evolutionary security strategy can overcome such threats and provide 360º protections against attacks.
4 min read
Jan Lindquist : 20. November 2023

In today's digital landscape, ensuring the security of your mobile applications is paramount. Cryptomathic's Mobile App Security Core (MASC) is at the forefront of mobile app security solutions, designed to safeguard valuable digital assets on both iOS and Android devices.
With MASC, app developers can focus on creating exceptional business applications, while entrusting the vital security aspects to this platform-independent security solution. MASC seamlessly integrates into both new and existing apps, along with their corresponding backend components. This blog post guides you through the components of MASC, illustrating how to move from basic to state-of-the-art protection for both your customers' and your business' invaluable digital assets.
To get the state-of-the-art protection these are the steps for full app integration with MASC:
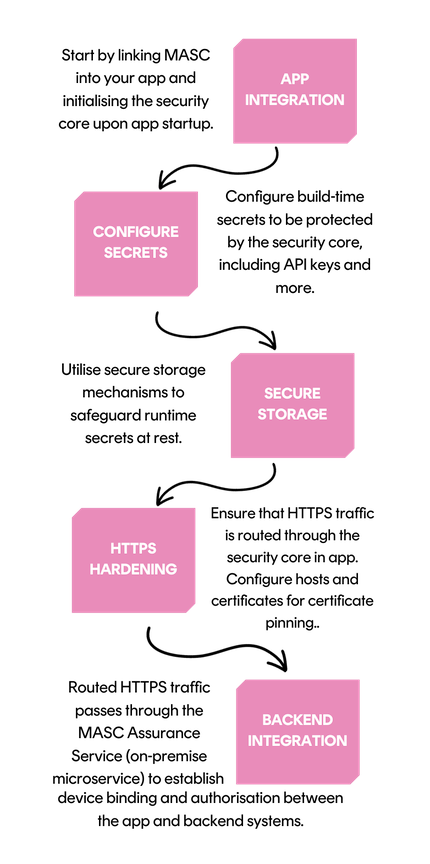
In the following sections, we will describe the protective measures achieved through these integration steps:
-1.png?width=740&height=347&name=Untitled%20(1920%20x%20900%20px)-1.png)
Once MASC SDK is integrated with your app, several protection mechanisms become active without the need for backend system integration or specialised app configurations. The activated safeguards include:
MASC continuously monitors your app to identify debugging attempts and execution of the app in emulated environments, protecting it from runtime analysis. When debugging attempts are detected, MASC can deliberately crash the application process to prevent further debugging attempts.
MASC employs various techniques to detect signs of code tampering: monitor for changes to code checksum, detection of function hooking or function replacement or hooking frameworks, etc.
Both MASC anti-debug and anti-tamper mechanisms can detect common hacking tools and respond appropriately upon detection.
Rooted or jailbroken devices are often used for reverse-engineering, and offers less protection of users against malware. MASC continually detects signs of the device being jailbroken or rooted. The detection results can be relayed to the backend via health and audit messages (see below) and can be used to deny or limit access from potentially compromised devices.
Android and iOS emulators are also often used in reverse-engineering as mentioned in detecting anti-debug. MASC looks for signs of emulator usage, and it not only can crash the app but also notifies the backend.
Mobile apps frequently require build-time static configurations like license keys, API keys, backend host names, certificates etc. MASC includes a build-time tool for obfuscating highly sensitive static configuration data, ensuring they remain encrypted at rest and providing a safe runtime API to access the configuration data.
MASC provides secure storage and independent cryptographic functions, building upon and extending the key stores provided by the device OS. The MASC secure storage may be used to safeguard critical cryptographic keys, such as application and communication keys, and prevents data separation from the application or data migration to other devices.
Both the app and backend systems require assurance of each other’s authenticity. MASC achieves this through API and Device Assurance.
API Assurance controls access to protected backend APIs and enhances confidence that the backend communicates with a genuine app instead of using a simple key which can be copied and reused.
This security mechanism introduces several layers of obfuscation in the build process for protection of assurance building blocks. A challenge-response protocol based on these assurance building blocks assures the server that it talks to a genuine app. This also serves to protect the server API from unauthorized access, by preventing non-approved 3rd party apps or aggregators from accessing the APIs, at the outer perimeter.
Device binding can be established after initial contact between a newly installed app and backend systems. The binding protocol authenticates the app and the backend systems to each other without sending shared secrets across the network. Device-unique keys are negotiated to protect future communication with the specific device and identify it on subsequent encounters.
Mobile apps' most vulnerable interface is communication with the backend. MASC is designed to secure communication from any monitoring between the business app and the backend systems. It facilitates the setup of a separate root certificate store (independent of the device certificate store), implements server certificate pinning, and offers a range of security measures that can be configured independently or jointly for maximum security. These are some of the steps taken to secure the communication:
HTTPS traffic to the backend must be tunnelled through MASC to be able to use the keys controlled by MASC. This means that an attacker cannot just circumvent MASC. The HTTPS tunnelling applies a whitelist to the host names and certificates (certificate pinning) presented by the hosts to further prevent man-in-the-middle attacks. The whitelists are provisioned to MASC and kept protected to prevent access and modifications by an adversary.
MASC optionally adds an extra layer of transport encryption on top of TLS to safeguard against TLS man-in-the-middle attacks or to be used when end-to-end encryption is required.
Access token protection and replacement ensure that OAuth2 access tokens are securely stored and managed exclusively within MASC, without exposing them to the upper app layers.
MASC allows the configuration of a set of protected HTTP cookies. The protected cookies are stored and managed exclusively inside MASC, and are therefore not accessible to the upper app layers. This can be useful to protect for example secure session cookies.
MASC allows updates of configured items to be triggered remotely for rapid response to compromises or host name and certificate changes.
MASC continuously monitors the app and software components for signs of debugging, tampering, and device rooting or jailbreaking. Gathered information can be transmitted to the backend through device health and audit log APIs, enabling the service owner to make informed decisions about denying or limiting access based on device integrity.
In a world where mobile apps are central to business operations and customer engagement, the security of these applications cannot be taken lightly. Cryptomathic's Mobile App Security Core (MASC) offers a comprehensive solution, seamlessly providing a range of protections that can take your app's security from basic to state-of-the-art with relatively little effort. By implementing MASC, you not only protect your customers' invaluable digital assets but also fortify your business against evolving security challenges.
Understand the threat landscape and how MASC's evolutionary security strategy can overcome such threats and provide 360º protections against attacks.
Comprehensive and dynamic
protection for mobile applications that handle sensitive data
Delve into the use cases and best practices for safeguarding sensitive customer data on mobile apps using the European Digital Identity Wallet (EUDI Wallet).