3 min read
Key Management Challenges in Financial Symmetric Cryptography Systems
Cryptomathic : 04. April 2022

- Home >
- Key Management Challenges in Financial Symmetric Cryptography Systems
This article addresses some of the challenges of symmetric cryptography as applied in banks, describing how it works and what are its unbeaten advantages as opposed to asymmetric cryptography.
Some major challenges of symmetric cryptography
Firstly, the complexity of key management grows significantly with every additional user that requires access to the secret key to encrypt or decrypt data. If you have several users that require access to the secret key, you may require some special processes.
Also, symmetric keys have no metadata inherently attached to a key - therefore key expiration tracking and rotation must be maintained by an additional tool (such as a central key-lifecycle management system).
Furthermore, unauthorized disclosure of one symmetric key makes all users/subscribers vulnerable - therefore symmetric keys need to be protected by highly secure storage units, such as Hardware Security Modules (HSMs). At the end of the key lifecycle, the key should be updated to a new key and the old one terminated or retired for all users.
Symmetric and asymmetric cryptography
 The symmetric scheme for cryptography has existed since ancient times.
The symmetric scheme for cryptography has existed since ancient times.
There is a “secret” or a “key”, which is used to encrypt and decrypt. This key must be protected.
The asymmetric cryptographic scheme appeared after 1970. The idea here is to use one key to encrypt, and another to decrypt.
The asymmetric scheme, with variations, is widely used for protecting online communications nowadays. Public Key Infrastructure (PKI) is implemented everywhere and uses asymmetric cryptography.
There are people or organizations, such as the military, who do not trust asymmetric schemes. Why so? There is a strong reason for this disbelief - a weak mathematical basis. Asymmetric cryptography relies on “computational complexity”. On the other hand, symmetric schemes are mathematically proven. Computational complexity is always “relative” or “comparable”, therefore your enemy/attacker could possibly be more powerful than you. For example, you might use a 2048 bit RSA key, but they could use IBM Parallel Sysplex (parallel processing through a cluster of high performing computers) to crack your cipher.
Despite some potential weaknesses, asymmetric cryptography is widely used and will continue to be used due to its advantages over symmetric schemes.
How does the symmetric scheme work in reality
Symmetric scheme devices are bulky and not user-friendly. They were designed to resist any exploitation attempt. Typical fields of application are banking or military grade equipment.
How does it all work? Imagine we have 2 devices, designed to maintain a point-to-point encryption channel of some kind. Each device has a few symmetric keys:
- A master key or keys. This one is a long-term, highly physically protected key, used to decrypt other keys
- KEK - a key encryption key. Also heavily protected. Long-term stored.
- Session or block key. Generated on board by a hardware random number generator.
 The master key or keys should be updated periodically, e.g. every year. Changing master keys is impractical. The cryptographic device periodically checks a master key's integrity.
The master key or keys should be updated periodically, e.g. every year. Changing master keys is impractical. The cryptographic device periodically checks a master key's integrity.
KEKs are installed by a security officer or in an automated arrangement by a key management system. A key distribution center sends a KEK, encrypted by the master key.
The device decrypts the KEK and stores it. If the device has data to encrypt, it performs the following actions:
- Creates a session key using a Hardware Random Number Generator
- Encrypts a small amount of the data on the session key
- Encrypts the session key with the KEK and taking certain precautions (key expansion and wrapping)
- Sends the encrypted data and encrypted KEK to the other side. Basically the dispatch is performed by different equipment.
- Destroys session keys
- Every N kilobytes of plain input data we have to re-create session key and repeat steps 1-3.
- A receiving party gets an encrypted piece of data, and an encrypted session.
The scenario can vary, but the problems remain the same.
There are many practical problems arising in this scenario:
- How can we keep master keys secret and protected for a long time?
- KEKs have to be rotated periodically - How often? By who?
- KDC - Key Distribution Center - must be used - how to secure a delivery channel from a KDC to a subscriber?
- Every communication link between the two subscribers has to use a common key (in this scheme - a KEK). The challenge is how to rotate these keys at the same time in all equipment, owned by all subscribers.
Why is the symmetric scheme still in use?
Symmetric algorithms resist any exploitation attempts, and are until today not matched by any other encryption scheme. In addition, due to the short recommended key length and the simplicity of the algorithm, data processing is much faster and thus economic than asymmetric encryption.
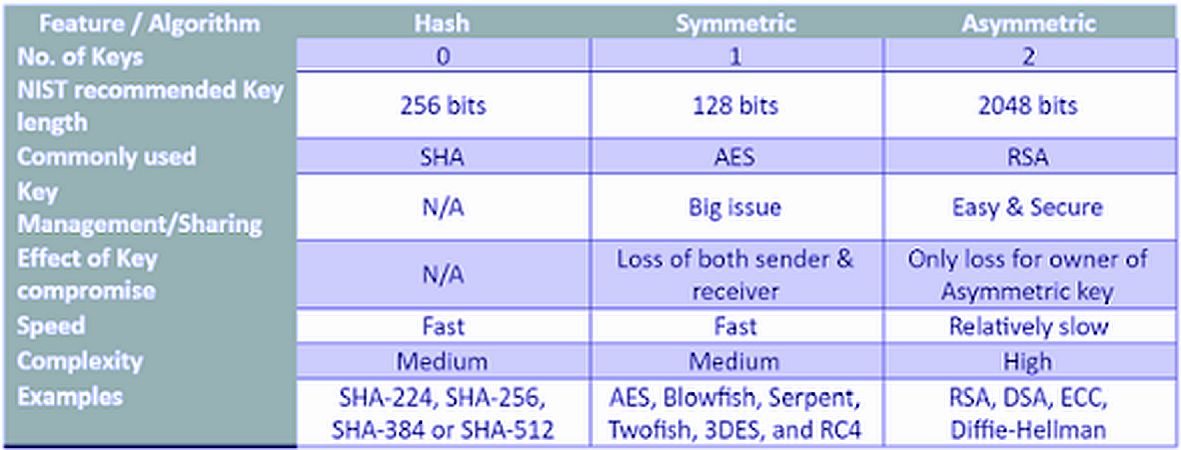
Imagine the millions of concurrent transactions done in the frame of payment card handling or during financial transactions. It is vital to have a fast and highly safe scheme. Symmetric key encryption is the right fit here.
But how do we handle the complex key handling challenges?
Cryptomathic CKMS
Let us turn the challenge into a feature. Cryptomathic provides an industry-grade Crypto Key (lifecycle) Management System (called CKMS), built around a hardware security module (or a cluster of hardware security modules). This system automates all the tedious management tasks and also provides comfortable and auditable analysis and logs at a central place. So the compliance audits, like PCI-DSS, are facilitated as well.
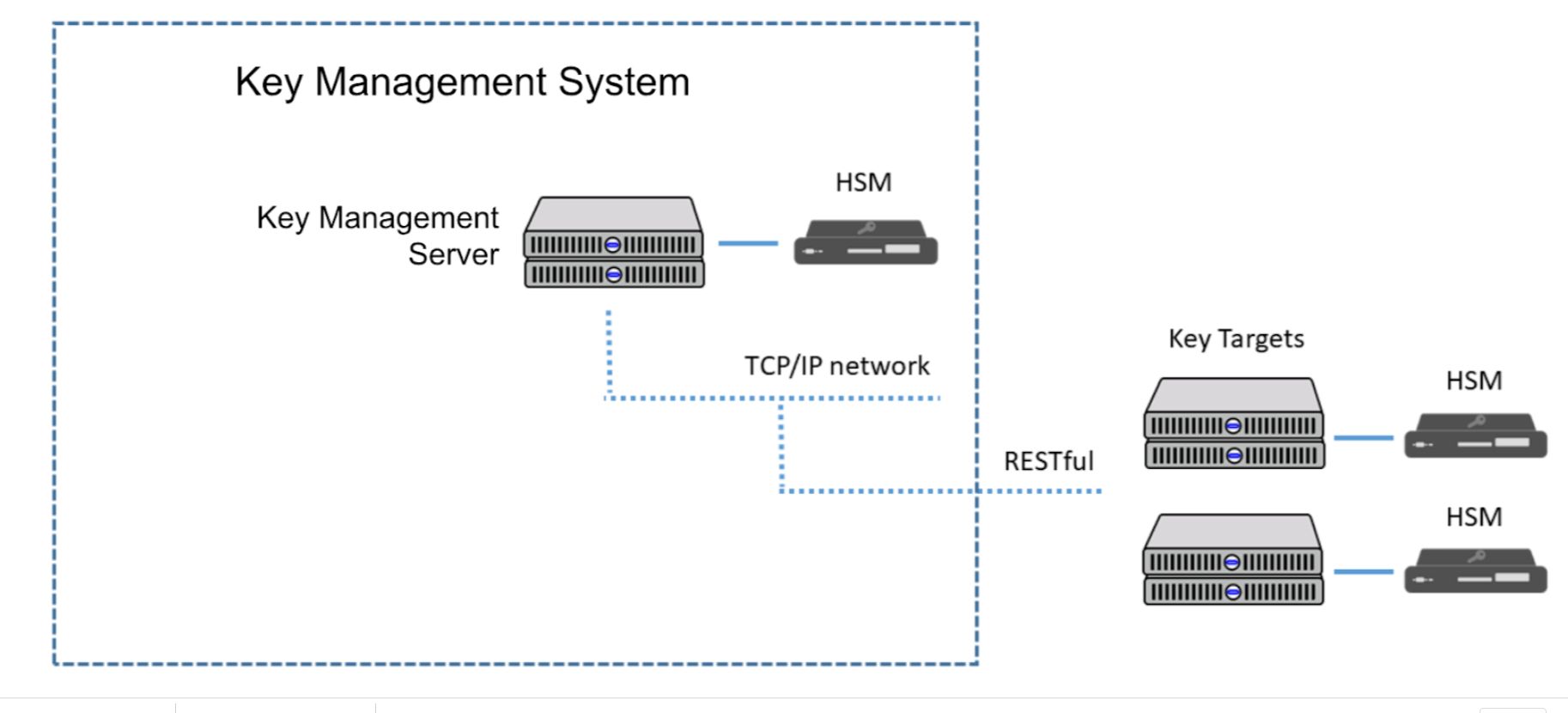
With such a key management system, symmetric keys can even be distributed into the most remote peripherals of a corporate or intercorporate architecture without compromising security.
Conclusion
Symmetric key schemes proved to be the right choice for banking-grade security, well outbalancing the disadvantages compared to asymmetric cryptography. Professional banking-grade key management systems like CKMS help compensate for the disadvantages of asymmetric cryptography and turn them into advantages.
References and Further Reading
- Symmetric Key Encryption - why, where and how it’s used in banking (2019), by Peter Smirnoff & Dawn M. Turner
-
Selected articles on Key Management (2012-today) by Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
- Selected articles on Key Management in the Cloud (2017-today) by Edlyn Teske, Matt Landrock, Rob Stubbs, Stefan Hansen, Ulrich Scholten, Joe Lintzen and more
