4 min read
Benefits of an Automated Centralized Key Management System
Cryptomathic : 02. October 2018

- Home >
- Benefits of an Automated Centralized Key Management System
The aim of this article is inform you on how to implement proper key management and to answer 3 important questions regarding centralized and automated key management:
- What is Centralized Key Management?
- How can a centralized system help meet regulatory compliance?
- How can automation further improve the life cycle management of keys?
Distributed key management systems make it very difficult to manage cryptographic keys. As your company grows, so does your data and the number of encryption keys you must manage to maintain data security.
By switching to a centralized key management system, you will remove these challenges, increase life cycle efficiency, and help your IT departments develop proper key management policies that scale with your organization.
First, let’s take a look at what it means to practice proper key management.
Proper management of cryptographic keys in hardware security modules.
Proper key management is an essential process of data security within any organization handling sensitive information. To avoid risks and efficiently scale operations, an organization should centralize its key management systems. This will result in good key generation and ensure key integrity within the system.
How to implement proper centralized key management policies and procedures:
- Develop secure data policies within your organization
- Define the processes necessary to implement those policies
- Automate those processes for your hardware security modules with a dedicated KMS.
What is a Centralized Key Management System?
A centralized KMS offers more efficiency as opposed to a distributed or application-specific KMS. They are called centralized because they use a single point to secure key management, policies and access audit logs. To boot, your organization can develop uniform key management procedures across all of your departments.

Some benefits of a centralized key management system:
- Provides tamper evident records for proof of compliance
- Streamlines key management processes and reduces costs
- Automatic key updates and distribution to any end-point
- Reduces the risk of human errors with user & admin permissions
- Dual control with asynchronous workflows
- System-wide key control manages any key type and format
- Offers High availability and scalability
- Reduces costs with automation
- Simple backup and recovery
Another key advantage of implementing a centralized system — it eases regulatory compliance by providing a complete record of every time a sensitive operation or key activity is administered from the server.
How can a centralized system help meet regulatory compliance?
Regulation is a topic brought up in any serious discussion regarding data security. Anytime sensitive information storage is involved, you must follow the standard security rules required by an exhaustive list of compliance authorities. The particular regulations/security standards relevant to encryption and key management depend on the type of information that is being stored or processed and what sector the business operates within. In order to pass compliance testing and audits, you need to keep your data security procedures documented and updated. For most companies, compliance can be a major hassle.
Here are some of the standards to consider for HSMs:
- Federal Information Processing Standard (FIPS)
- Common Criteria Evaluation Assurance Levels (CC EAL)
- Payment Card Industry - Data Security Standards (PCI DSS)
 Key management systems are typically developed with certain sectors/industries in mind, and therefore it is advisable to choose a centralized KMS that has a proven track record for supporting the security/regulatory standards of the particular sector that is relevant to the business.
Key management systems are typically developed with certain sectors/industries in mind, and therefore it is advisable to choose a centralized KMS that has a proven track record for supporting the security/regulatory standards of the particular sector that is relevant to the business.
A centralized KMS can help passing compliance audits by enforcing the security policies and automatic logging of all security sensitive operations. A unified overview and central control of all the essential logs makes demonstrating compliance much easier and quicker than auditing various disparate key management systems.
Compliance is non-negotiable. It is equally important for the system to support the complete life-cycle of cryptographic keys. Automating key management further reduces the need for time-consuming, manual key functions.
A system that puts high value keys under management needs to centralize, automate and optimize the encryption key management process through the entire life cycle. Proper management reduces overhead costs, ensures generated key quality, and protects these keys in storage and in transit.
How can automation further improve the key management life cycle?
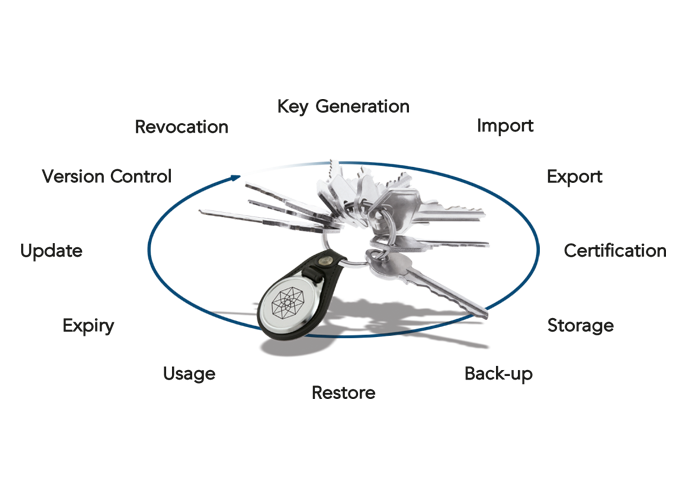
It is inefficient for skilled technicians to manually manage the key's life cycle. The illustration below highlights some of the stages of a key’s life cycle.
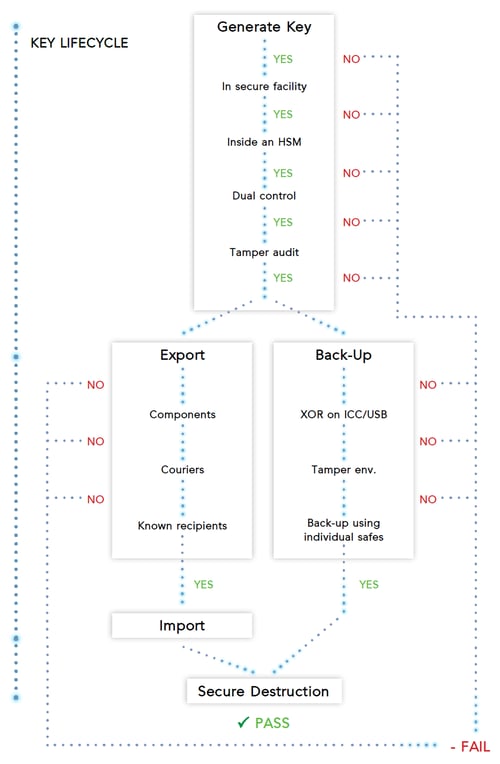
A centralized system featuring automated key management saves labor resources and allows them to concentrate on more important responsibilities.
For example, you can automate the key import/export process, so systems can exchange keys via a push/pull protocol.

Helps to avoid human error
Human error is hard to avoid. For key management, this include mistakes in installing and maintaining devices, typing key components, and integrating with applications securely. To reduce reduce the risk of human error compromising sensitive data, an enterprise can switch from manual key management to an automated process (for both key administration and audit logging).
Streamline your key management life cycle
This will also increase the efficiency of your security procedures, and allow for easy backup and recovery, if a key is lost or compromised. An automated process allows the company to streamline the entire life cycle of key management, including everything from generation and distribution to expiration. Backups, recovery, and destruction. Key and certificate updates can be handled in just a few clicks.
How it works
A centralized KMS should be straightforward, secure and versatile. It should enable easy automation of key and certificate generation and distribution to any endpoint. The process is similar in most systems. Here's how it works for web servers.
- As the server certificate is about to expire, the centralized KMS will generate and distribute a new key and certificate.
- To ensure integrity of the system, two people are needed to log in to the centralized KMS using smart cards and PIN entry devices (PEDs) either together or asynchronously. Updating the certificates a distributing keys takes just a few clicks.
- The new key automatically updates and sends the certificate signing request to CA for key certification.
Once received, the CA validates the certificate and returns it back to the Centralized KMS users, who push the new key and certificate to the endpoint.
That's it! The server now uses the updated key and certificate. With centralized KMS secure key distribution takes minutes not hours.
References and Further Reading
-
NIST SP800-57 Part 1 Revision 4: A Recommendation for Key Management (2016) by Elaine Barker
-
Selected articles on Key Management (2012-today) by Ashiq JA, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
-
CKMS Product Sheet (2016), by Cryptomathic
