3 min read
Countdown to compliance: DORA is live, PCI DSS 4.0 is in force, and PQC readiness for financial institutions
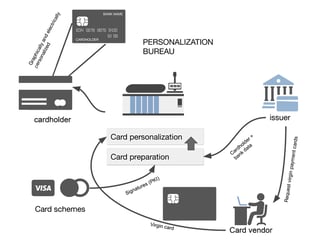
Financial institutions are facing an unprecedented convergence of compliance pressures and technological challenges. With the European Union’s DORA,...