3 min read
How Cryptomathic’s MASC Strengthens Mobile Payments and Ensures PCI DSS and PSD2/3 Compliance
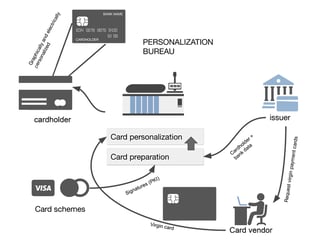
With the increasing adoption of mobile banking and payment apps, financial institutions face greater challenges in securing cardholder data. The...