4 min read
An Expert Introduction to z/OS & IBM Cryptographic Architecture
IBM’s mainframe computers have been a rock-steady part of banks’ security infrastructure for many years. Originating from the local data-center...

4 min read
IBM’s mainframe computers have been a rock-steady part of banks’ security infrastructure for many years. Originating from the local data-center...

4 min read
The use of mobile payments is expected to continue to rise and become the second most popular payment method after debit cards by 2022. Analysts...

3 min read
This article addresses some of the challenges of symmetric cryptography as applied in banks, describing how it works and what are its unbeaten...
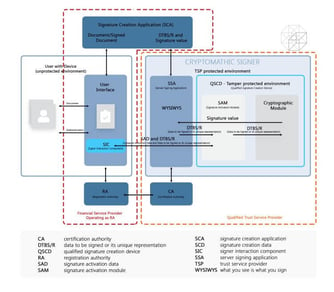
3 min read
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...

3 min read
Banks continue to feel the profound transformational effects that digital technologies have on their business. This can be seen in the creation and...

3 min read
What You See is What Your Sign (WYSIWYS) is a term that is used to describe an enhanced level of data integrity within a digital signature system....

4 min read
In this article, we will discuss the Certificate Authority (CA) in the context of eIDAS and what is required of this entity in ensuring the integrity...

4 min read
Considering the COVID-19 impact on digitalization, EBA’s updated Guidelines on ICT and Security Risk Assessment will help focus on priority areas,...

5 min read
Open banking can offer opportunities for retail banks that are faced with competition from newcomers to the banking and finance industry. For those...