1 min read
Signer 6: A Game-Changer in Digital Signing Solutions
signer 6 enables future-proofed, scalable digital signing to support the upcoming european digital identity wallet (eudi) We are delighted to...

1 min read
signer 6 enables future-proofed, scalable digital signing to support the upcoming european digital identity wallet (eudi) We are delighted to...

5 min read
Achieve Non-Repudiation of Origin (NRO) and Non-Repudiation of Emission (NRE)
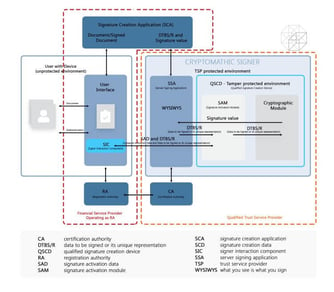
3 min read
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...

4 min read
In this article, we will discuss the Certificate Authority (CA) in the context of eIDAS and what is required of this entity in ensuring the integrity...

4 min read
Cryptographic algorithms can be categorized into three classes: hash functions, symmetric, and asymmetric algorithms. This article sheds light on...

3 min read
Non-repudiation is a legal concept that is widely used in information security. It refers to any service which provides proof of the origin of data...

3 min read
This article sheds light on the two approaches to achieve non-repudiation of an electronic message: non-repudiation of emission and non-repudiation...

5 min read
Have you ever heard the kind of sweet and innocent voice saying, “I didn’t eat my brother’s ice cream”, while the kid’s mouth and t-shirt are covered...