4 min read
Understanding the Certificate Authority in the Context of eIDAS
Cryptomathic : 05. January 2021

- Home >
- Understanding the Certificate Authority in the Context of eIDAS
In this article, we will discuss the Certificate Authority (CA) in the context of eIDAS and what is required of this entity in ensuring the integrity of qualified electronic signatures.
To have confidence in the authenticity of electronic signatures, users need to have confidence that the CA follows proper procedures and protective measures to minimize both operational and financial risks and threats commonly associated with public-key cryptosystems.

Electronic commerce continues to emerge as a preferred method of doing business and communicating across private and public networks.
To do this securely, one of the requirements of electronic commerce is to identify the original source of the electronic information to be as trusted. The methods most used for this are electronic/digital signatures backed by the credibility of a certificate issued by a CA.
The European Union’s eIDAS Directive establishes a framework for qualified electronic signatures that rely on the security provided by a qualified certificate. Annex I of eIDAS specifies requirements for qualified certificates. Annex II of eIDAS specifies the requirements that certificate authorities must follow in issuing qualified certificates.
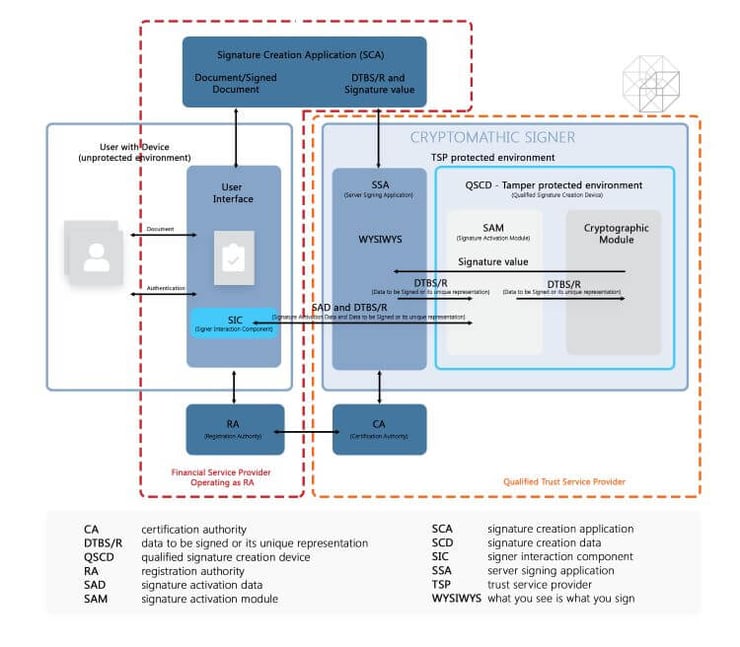
The infographic above gives a general overview of where the CA sits within the trust service architecture in relation to the remote signing process of qualified electronic signatures.
Terms to Understand
To avoid confusion, it is essential first to understand the following terms and their relationship between eIDAS and electronic signatures.
Certificate Authority
A CA is an authority trusted by one or more users to create and assign certificates for use with their electronic signatures.
Certificate
A certificate is the user’s public key combined with additional information, e.g. to identify the user, which is then enciphered with the certificate authority’s private key to render it unforgeable.
Certificate Policy
A certificate policy is a specified set of rules that dictate a certificate's applicability to a particular use according to common security requirements.
Qualified Electronic Signature
A qualified electronic signature is an advanced electronic signature based on a qualified certificate created by a secure-signature-creation device as specified under eIDAS.
General Concepts of Certificate Authorities
Certificate authorities possess the overall responsibility for providing certification services, including:
- Registration
- Certificate generation
- Dissemination
- Revocation management
- Revocation status
- Subject device provision (optional)
The CA is identified in the created certificate as its issuer, while its private key is used in signing user certificates.
Certification authorities must ensure that all requirements are implemented according to the selected qualified certificate policy. They are responsible for conforming to the procedures laid out in the qualified certificate policy, including when a subcontractor performs the CA’s services. The CA must provide all its certification services according to its certification practice statement.
A certification authority may also use other parties to provide parts of the certification service. For instance, a CA may subcontract all the services required to create a qualified electronic signature. However, it maintains the overall responsibility and must ensure that all policy requirements are met as specified under eIDAS.
Certification Authority Practice Requirements
The certification authority must implement controls that meet the following requirements in its Certification Practice Statement (CPS), including:
- Having a statement of its practices and procedures used in addressing identified requirements in the qualified certificate policy.
- Identifying all external organizations' obligations that support the CA’s services, including all applicable policies and practices.
- The CA’s certification practice statement and any other relevant documentation as needed to conform with the qualified certificate policy is made available to subscribers and involved parties.
- Disclosing to all subscribers and potential relying parties of the terms and conditions for using the certificate.
- Having a high-level management body that holds the final responsibility and authority for the certification practice statement's approval.
- The senior management's responsibility is to ensure that the CA’s established certification practices meet the specified applicable requirements specified under eIDAS and are implemented properly.
- Giving due notice of changes it plans to make to its Certification Practice Statement, and following approval, make the CPS immediately available as required.
- Documenting the signature algorithms and parameters used.
3 Deployment Options from self-managed CA to outsourced CA-as-a-service
The role of the CA is normally tied to the trust service provider. It could either be located in and operated by your institution, or it could be outsourced to an external partner in the frame of a 3rd party trust service provision.

An approach often seen in the market is that financial service providers pass customer data directly through to a 3rd party signing service company to avoid all administrative and legal burden. Doing so, they give away one of their strongest assets: customer data. The 3rd party signing service provider will benefit from it over time through aggregation of data of the same customer from various sources. Eventually the service provider may carry off the pole position on customer insight, such as risk assessment data or specific needs.
We strongly advocate against such solutions and suggest options, which are beneficial to financial institutions in the short and long run.
Cryptomathic makes remote signing available in three different variants, allowing banks to operate as:
- Full Trust Service Provider
- Trust Service Provider “light”
- Signing Service Provider

Figure: Implementation / Delivery Options
Look at the following article to select the most suitable option for your company or institution.
References
- Selected articles on eIDAS (2014-today), by Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner, and more
- ETSI TS 101 456 V1.4.3 - Electronic Signatures and Infrastructures (ESI); Policy requirements for certification authorities issuing qualified certificates (05. 2007), by the European Telecommunications Standards Institute ETSI
- CEN/TC 224 - Trustworthy Systems Supporting Server Signing Part 2: Protection Profile for QSCD for Server Signing (05.2018), by AFNOR
- Conformity assessment of Trust Service Providers - Technical guidelines on trust services (2017), by the European Agency for Cyber Security
- Mutual Recognition Agreement of Information Technology Security Evaluation Certificates, VERSION 3.0 (Jan, 2010), SOG-IS
- Trustworthy Systems Supporting Server Signing Part 2: Protection
Profile for QSCD for Server Signing (2019) by CEN/TC 224 - About The Common Criteria (retrieved October 2020), by Common Criteria
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission