3 min read
The Reasons Why a Banking KMS Must Support Atalla Key Blocks
 Martin Rupp (guest)
:
30. June 2020
Martin Rupp (guest)
:
30. June 2020

- Home >
- The Reasons Why a Banking KMS Must Support Atalla Key Blocks
Invented by Mohamed Atalla, the Atalla key block is the root of all key blocks. All over the globe, hundreds of millions of financial transactions are secured daily using hardware security modules (HSMs) and the Atalla key block format that follows TR-31 guidelines. Here we will explain a bit about AKB and why a banking-grade key management system (KMS) must support it.
Overview of the Atalla Key Block
In principle, HSMs use key block structures to achieve secure key management. A key block (or key bundling) is a data structure used to store or exchange cryptographic keys within hostile environments.
As a minimal requirement:
- Key blocks should be encrypted
- Hardware security modules should be able to determine the correct key usage via control information
- Tampering should be detected via a dedicated secure mechanism
The Atalla key block was the first implementation of a secure key block that met these requirements.
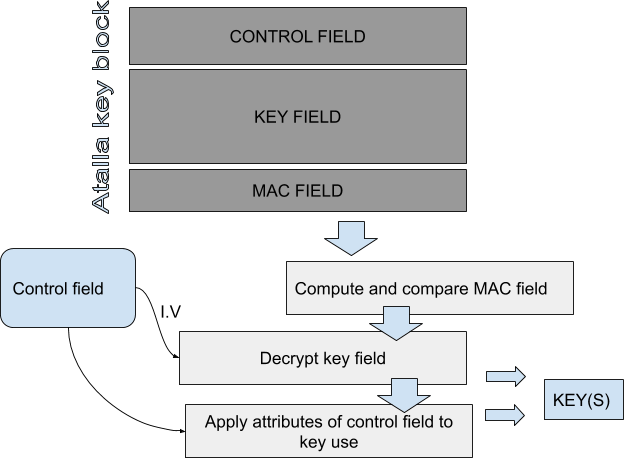
A key that is secured by the Atalla key block consists of three parts:
- An 8-byte header containing the attributes of the key (header);<
- A 48-byte key field containing the Triple-DES cipher block chaining (CBC) mode ciphertext of the key (encrypted key field);
-
A 16-byte field containing the Triple-DES message authentication code (MAC) computed over the header and the encrypted key field.
The Atalla key block was the origin of several standards. Therefore, its format is de facto in corporated into the following standards:
-
ANSI X9.24 Part 1-2017 Retail Financial Services Symmetric Key Management Part 1: Using Symmetric Techniques
-
ANSI X9.24 Part 2-2016 Retail Financial Services Symmetric Key Management Part 2: Using Asymmetric Techniques for Distribution of Symmetric Keys
-
ANSI X9 TR-31, Interoperable Secure Key Exchange Key Block Specification
Here we detail how the Atalla key block (AKB) is processed by a receiver to extract the key (or PIN) it protects.
Firstly, the AKB is integrity checked by computing the MAC and comparing it to the presented MAC field. If the MACs are the same, the operation continues. The key is then decrypted using the Control Field Initialization Vector I.V) and the first variant of the master file key. Keys are then resolved and used following the data from the control field. The control field is an 8-byte header which details all the information about the key within the block.
|
Byte |
Description |
|
0 |
Version number for the format |
|
1 |
Key usage |
|
2 |
Algorithm |
|
3 |
Mode of use |
|
4 |
Exportability |
|
5 |
Padding flag |
|
6 |
Special handling information |
|
7 |
Other information |
Table: key information contained in control field header
As you can see, a lot of information is presented in the header which makes AKB very flexible for different use cases.
The key usage can be one of the following options:
- ATM master key
- CVV
- Data encryption
- IV
- Key encryption
- MAC
- Manufacturer-defined
- PIN encryption
- Reference PIN block
- Signature
- Token key
- PIN Verification
- Translation and conversion table
- Communication key
- Derivation key
- Master key
- Diebold number
The AKB can handle the key for the following algorithms:
- Manufacturer-defined
- SHA-1
- RC2/MD2
- IBM 3624
- RC4/MD4
- RC5/MD5
- IBM4731
- ANSI
- Atalla
- DES/3DES
- EMV key derivation
- Diffie-Helmann
- AES
- SSL
- RSA
- DSA
- VISA
- ECC
The Importance for a KMS to Understand the Atalla Key Block Format
In respect to the card payments and banking industry, it is vital for a key management system to be able to understand the Atalla key block format, so that keys wrapped by such a format can be imported and exported to and from the KMS - securely and in accordance with industry standards (PCI).
To understand the importance of the Atalla key block, you should be aware that it is the format used to protect 250 million card transactions daily. That adds up to more than 90 billion transactions each year since 2013. AKB has been used to secure much of the world's ATM transactions since 2014.
If you are dealing with cloud-based applications, standard key management systems from cloud providers do not understand the Atalla key block format. For example, Key Vault supports RSA and Elliptic Curve keys only. Therefore, it cannot deal with Triple-DES or AES key wrapping.
It is highly probable that your bank or financial organization is or will be using the Atalla key block format. As such, you should consider only buying a key management system that has an established support for the Atalla Key Block.
References, Side Notes and Further Reading
- Read more articles on key blocks (2019 - today), by Martin Rupp, Dawn M. Turner and more
- Read more articles on the ANSI X9.24-1-2017 (2018 - today), by Martin Rupp, Matt Landrock and more
- ANSI X9.24-1-2017 - Retail Financial Services Symmetric Key Management Part 1: Using Symmetric Techniques (2017), by the Accredited Standards Committee X9 (Incorporated Financial Industry Standards), American National Standards Institute
- ASC X9 TR 31-2018 - Interoperable Secure Key Exchange Key Block Specification (2018), by American National Standards Institute (ANSI)