4 min read
Issuing MULTOS Cards
MULTOS cards are being deployed in steadily increasing numbers and Cryptomathic is delighted to be involved in MULTOS projects across the globe....

4 min read
MULTOS cards are being deployed in steadily increasing numbers and Cryptomathic is delighted to be involved in MULTOS projects across the globe....

3 min read
The IBM mainframe series (“z-series”) has become a backbone for security, privacy and resilience in a large share of payment and banking related...
3 min read
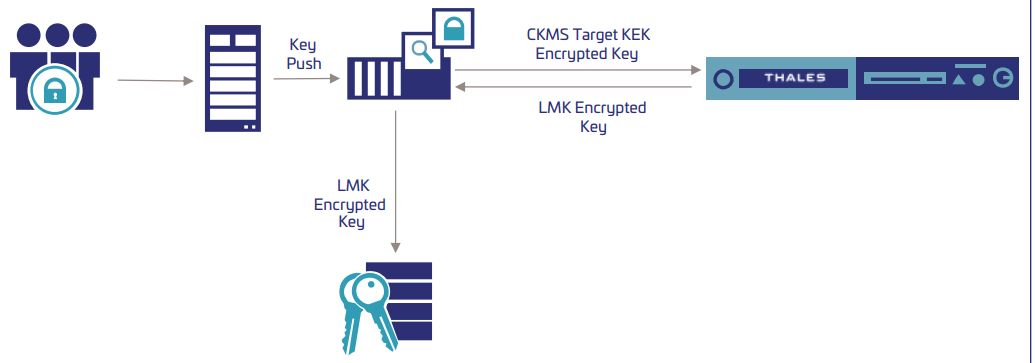
Thales Key Blocks are an essential cryptographic key wrapping format. In comparison to other key block formats, they are proprietary and only work...

3 min read
Banks and other financial institutions are playing a key role in countering global challenges like money laundering and terror financing.

3 min read
In our previous article on eID schemes in Nordic countries, we looked at some data showcasing the remarkable adoption and engagement rates for such...
2 min read
Banks and financial institutions must adhere to a rigorous set of security and regulatory practices to protect data, communications, and processes.

3 min read
This article examines how federated signing can help banks overcome some of the obstacles they face when onboarding customers online in the era of...

3 min read
The protection and secure management of cryptographic keys is crucial for ensuring that cryptography is used in the most effective way to keep data...

3 min read
In Part 1 of this series, we looked at the objectives or motives behind having an eIDAS-enabled digital onboarding process. In Part 2, we look at the...