2 min read
Key Management – A Question of Ownership
This article looks at the problems associated with key management that are common in many businesses today, where there is no clear ownership; then...
2 min read
This article looks at the problems associated with key management that are common in many businesses today, where there is no clear ownership; then...
3 min read
Unlike other operating systems like Windows, Linux, or OSX, both Android and iOS operating systems are usually shipped with built-in user rights...

2 min read
In a retail financial services environment, the compromise of a symmetric cryptographic key is a critical security breach. Such a situation is...

3 min read
The rise of quantum computing is expected to have significant impacts on both financial and technological considerations when evaluating...
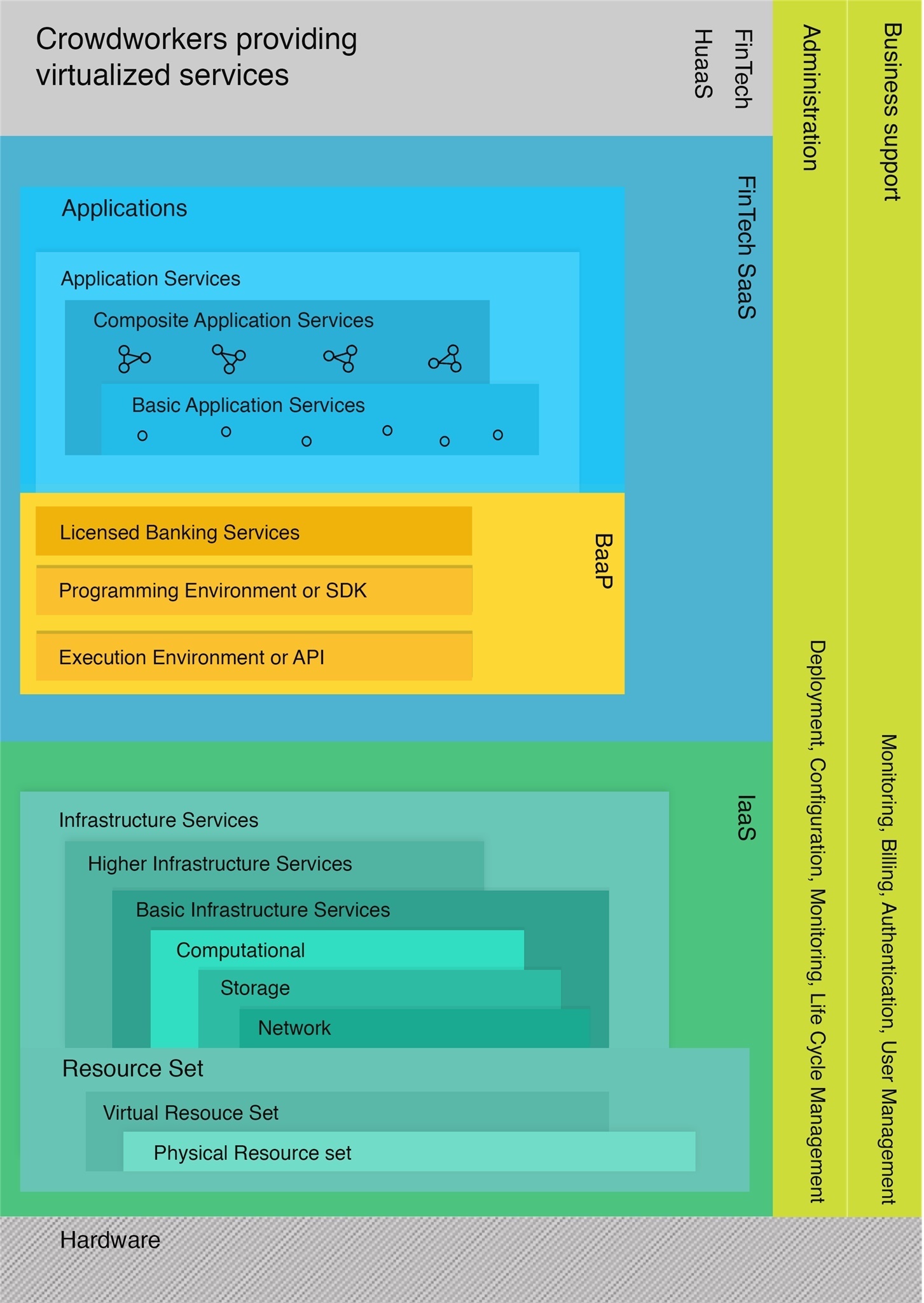
3 min read
Consumer behavior have shown a dramatic shift toward a preference for seamless digital banking solutions. Many banking customers now want simple and...

3 min read
With the ever-growing number of electronic transactions and documents, the use of digital signatures make it possible to trust and act upon these...

4 min read
In this article, we will discuss the Certificate Authority (CA) in the context of eIDAS and what is required of this entity in ensuring the integrity...

5 min read
Considering the COVID-19 impact on digitalization, EBA’s updated Guidelines on ICT and Security Risk Assessment will help focus on priority areas,...

3 min read
Securing data and keeping it private is essential for many organizations and institutions, including banks or ministries, where data security and...