3 min read
eIDAS & the European Interoperability Framework
The public sector accounts for a quarter of all employment and a fifth of the entire economic output of the European Union. Given the economic and...

3 min read
The public sector accounts for a quarter of all employment and a fifth of the entire economic output of the European Union. Given the economic and...

3 min read
Part 1 – Increasing Efficiency & Resilience This two-part article discusses how cryptography is employed within organizations today and examines some...
5 min read
Introduction Much has already been written about EU General Data Protection Regulation (GDPR), which comes into force on 25th May 2018 to protect EU...

4 min read
This article highlights the NIST key lifecycle recommendations in relation to PCI DSS compliance.

3 min read
"Banks aren’t places to store money anymore, banks are places to store data". This was the statement made by David Birch at the 2017 ISSE Conference...

2 min read
On the 9th of November, the Aarhus company Cryptomathic was awarded the Initiative Prize by the regional division of DI (Confederation of Danish...
3 min read
The "new economy" is the catch-all phrase encompassing all new mostly service based industries, especially the ones delivered on a digital platform.
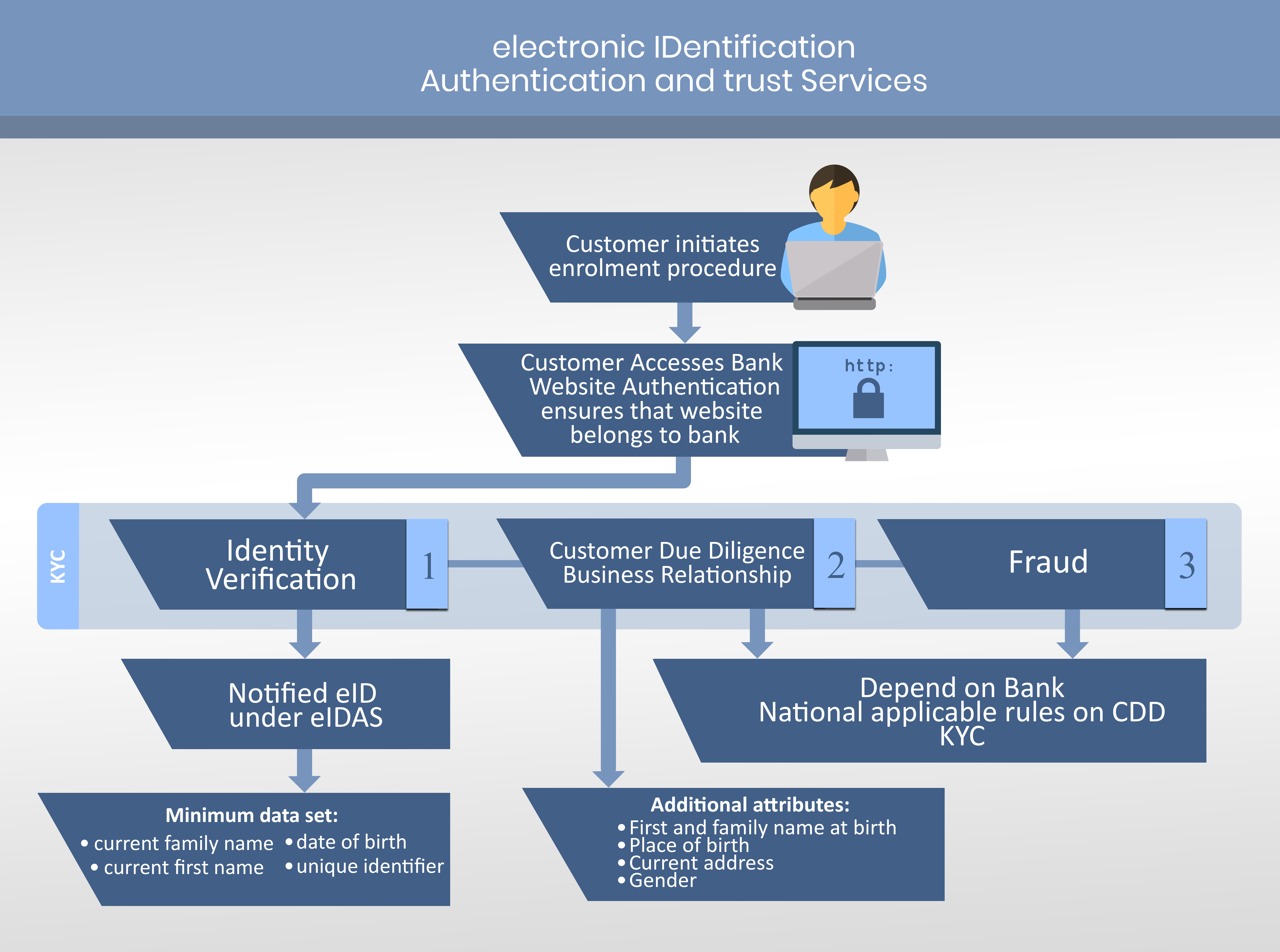
2 min read
Completely electronic means of identification and authentication are rapidly improving the way companies can offer services to customers digitally.

4 min read
This article outlines cryptographic operations and best practices you should follow to make your applications or systems secure.