6 min read
Enhancing Payment Card Security By Integrating PCI with EMV Technology
This article discusses how the security protection of payment card data used in a transaction can be maximized by integrating PCI DSS with EMV...

6 min read
This article discusses how the security protection of payment card data used in a transaction can be maximized by integrating PCI DSS with EMV...

3 min read
This article discusses methods of restoring secure systems, such as payment card processing, to normal cryptographic operation after an attack or...

2 min read
This article discusses the procedures and techniques used in key management system hardening for servers and devices.

3 min read
This article discusses the necessary exchange of information between entities within a security domain and other entities outside of the security...

3 min read
Cryptographic keys are used to secure data-at-rest and data-in-transit. Trying to keep them protected yet always available for use is one of the most...

4 min read
This article discusses the shortcomings and learnings from penetration testing of cryptographic key management systems for banking organizations.
6 min read
This paper discusses the various phases in the life cycle of a cryptographic key, and how the operational life-time and key strength can be...

3 min read
This article discusses key management strategies for the SaaS cloud model, and unique security problems to be dealt with because of lack of user...
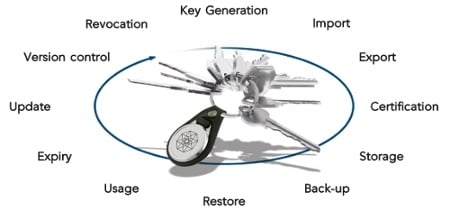
4 min read
Typical Services Provided by Key Management Systems Key management is the administration of tasks involved in all aspects of cryptographic key usage...