3 min read
Is Your Crypto Due a Service?
Recent revelations in the press have caused industry experts to question just how much trust can be placed in existing cryptographic standards or...

3 min read
Recent revelations in the press have caused industry experts to question just how much trust can be placed in existing cryptographic standards or...

3 min read
...continued from Part 1 The threat model Malicious mobile device hackers have a variety of goals. Foremost is monetary gain, but retribution,...
3 min read
With mobile devices being used for more credentialing based activities, the question of mobile security is becoming increasingly important. The...

6 min read
Introduction It is well-known and appreciated by most users - even if often ignored(!) - that if you choose a weak password, you are exposing...
6 min read
Introducing the TPM The Trusted Platform Module (TPM) is a special purpose microcontroller designed by the Trusted Computing Group, which interfaces...

2 min read
- hype or the answer to all our prayers? A couple of years ago, Craig Gentry produced a break-through result in cryptography: what researchers had...

3 min read
In 2004, Intel, Nokia, Panasonic, and Samsung, announced plans for a licensing and compliance framework called Content Management License...

4 min read
In 2009, the RBS WorldPay ATM network reportedly lost $9 million to a 30 minute fraud attack across 49 cities, in different countries, using just 100...
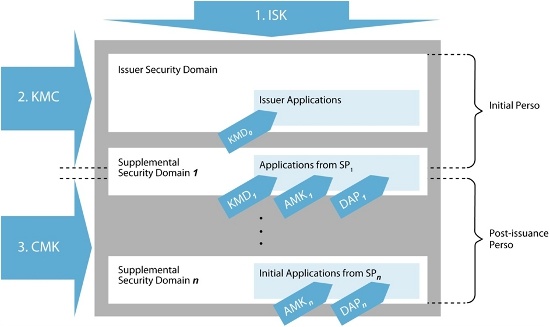
4 min read
This article provides an overview of GlobalPlatform (GP) Key Management and includes a proposed architecture for an efficient GP Key Management...