10 min read
Reducing Card Fraud with EMV Chip Technology
Cryptomathic : modified on 21. October 2015

- Home >
- Reducing Card Fraud with EMV Chip Technology
This article gives an insight into the EMV chip technology, which is being rolled out on a world-wide scale to increase the level of fraud protection in credit card transactions. It presents and discusses legal incentives for migration, security benefits, a detailed view of the sequence of steps in a transaction and a concluding discussion.
The necessity of the gradual shift to EMV technology
Because of its great potential for reducing fraud and better control of online and offline transactions, the migration from magnetic stripe based payment cards to EMV chip cards is an inevitable process that started about 20 years ago, and could span another 20 years or more. This move was originated by Europay (now part of MasterCard), MasterCard and Visa, and became abbreviated as EMV.
The transition to EMV chip cards was considered necessary because the magnetic-stripe cards are very vulnerable to fraudulent attacks due to counterfeiting (cloning cards by copying magnetic-stripe data), forging signatures, intercepting card data online, and many other types of attacks resulting from lost or stolen cards.
Most of these attack methods are rendered useless during EMV chip card transactions, because of advanced encryption techniques, embedded card risk analysis capabilities, and online and offline authentication and the impossibility of copying the chip-resident cryptographic keys used for transaction processing.
Motivation factors for the shift
The migration has been motivated by the increasing costs of correcting damages due to fraud, new liability regulations, widespread use of mobile devices, contactless connections, and other advances in technology.
As a result banks, issuers, processors, merchants, and others are working together to achieve a common goal, but at a relatively slow pace because of the extensive work involved in achieving it.
Migration at a global level
Approximately 80 countries around the world have already migrated to the EMV chip card technology, including Canada, Australia, UK, and various countries in Europe, the Middle-East, Latin America, Africa, and the Asia/Pacific region.
However, the U.S, which is the by far the largest user of payment cards and the largest target for payment card fraud, is lagging far behind in the conversion process.

U.S. Card Fraud Losses 2012 - 2014, Source: n>genuity journal
Incentives to speed up progress in the U.S.
Many incentives are now in place to speed up the migration process in the U.S. Credit card companies, including American Express, Discover, MasterCard and Visa have recently announced that they would accelerate their plans for moving to a chip-based payment infrastructure in the U.S.
Annual costs of card fraud is the main driving factor, which is estimated at $8.6 billion per year. If the U.S. continues to lag behind with its chip card implementation, costs could rise to $10 billion or higher in 2016.
Another major incentive is the Technology Innovation Program (TIP), as Visa expanded this program to the U.S. on October 1, 2012. This program eliminates the requirement for merchants to annually validate their compliance with the PCI Data Security Standard if certain criteria is met. This would save on maintenance and auditing costs, but the merchants would have to satisfy the following conditions:
- 75 percent of the merchant’s Visa transactions must originate from chip-enabled terminals
- Terminals must support both contact and contactless card interfaces, including mobile payments based on NFC technology.
- Merchants must ensure that their systems do not store track data, security codes or PINs, and other sensitive card data.
- Merchants must demonstrate that they continue to comply with the PCI DSS standards as applicable.
- The merchant must not have been involved in a breach of cardholder data. (Such a merchant may qualify again for TIP if it has subsequently validated PCI DSS compliance.)
In most regions, Master Card and Visa have set fraud liability shifts for bank issuers. “Liability shift” means that if issuers and merchants still are using non-EMV compliant devices, and they accept transactions made with EMV chip cards, they assume liability for any transactions that are found to be fraudulent on those cards. An important region that is still to shift is the United States.
The U.S. has been slow to adopt this program, but as of October 1, 2015, Visa intends to have instituted the liability shift program for all counterfeit card-present point-of-sale transactions in the U.S. Merchants with automated fuel dispensers will have an additional two years until the liability shift takes effect for them.

Roadmap to introducing EMV into the U.S.: POS Terminals,
Source: Mercator Advisory Group
Other added benefits inherent in an EMV chip card
There are also many other added benefits of switching over to EMV chip technology.
Magnetic strip data is fixed, while the data on an EMV chip can be dynamically updated, or “flash updated”, which helps to dramatically reduce costs over time.
Although chip cards are more expensive to produce, they have a longer shelf life than magnetic stripe cards, as the stripes tend to wear out. EMV chip cards were also designed to be used for multiple applications: for example, credit and debit capabilities on the same card as well as contactless capabilities.
Online security benefits
It is extremely difficult to counterfeit an EMV chip card because, unlike the magnetic stripe, the chip is able to do its own processing of information, as card authentication and PIN verification are done automatically by the chip for each transaction.
But the main feature that prevents fraudulent attacks is the use of “dynamic data” in that the card can generate its own unique “cryptogram” for each transaction, so that even if the card data is stolen or intercepted during a transaction, nothing can be done with it.
All dynamic card data can only be used for one individual transaction, and after that, it's useless. (See “Online processing” below for more information.)
Offline security benefits
Another major benefit of EMV chip cards over magnetic stripe cards is the ability to authenticate the card offline without the need to go on-line to the issuer.
Card issuers provide a choice of three different schemes for off-line authentication – Static Data Authentication (SDA), Dynamic Data Authentication (DDA), or Combined Data Authentication (CDA) (See “Offline processing” below for explanations of these).
All three schemes utilize the RSA (Rivest-Shamir-Adleman) cryptosystem, which uses public key cryptography, where messages can only be decrypted with a private key to maintain confidentiality. Only one of the three methods can be used for a particular transaction.
In addition to the card authentication and cardholder authentication provided by the RSA algorithm, the EMV specification requires that each EMV card use a unique 3-DES key to evaluate the actual transaction information between a card, a terminal and a bank.
The specification also requires the use of the SHA-1 (Secure Hash Algorithm) for the data integrity verification.
Sequence of events during an EMV transaction
For a magnetic stripe card, the card's permanently stored data is simply read by the terminal, and then the card is removed and no longer used for the transaction. The processing is done by the terminal while applying criteria for payment. During an EMV transaction, the chip itself will process information, and actually sets up a series of events for the transaction.
These events include offline data authentication, online authorization, verifying the cardholder identity via signature or PIN, etc.
The EMV specifications define the sequence of steps, which is the protocol for the interaction between the chip and the terminal. The following list describe these steps in more detail:
Application Selection – If there is more than one application in the chip, a selection process chooses a suitable application for the transaction, if it is supported by the terminal. The cardholder usually makes the choice here.
Initiate Application Processing and Read Application Data - The terminal reads cardholder data and sensitive application data from the chip, while using the selected application.
Offline Data Authentication - Offline Data Authentication is performed via SDA, DDA, or CDA. (See “Offline processing” below.)
Processing Restrictions – Additional Checks are made to for any restrictions in allowing the transaction requested by the chip.
Cardholder Verification – The cardholder is verified by a method that is mutually supported by the chip and the terminal. Methods can include signature, online PIN, offline PIN (plaintext or encrypted) or “no CVM” (cardholder verification method).
Terminal Risk Management – The terminal runs a few checks (such as spending limit) to determine the risk level, which may require online processing.
Terminal Action Analysis – The terminal application now analyzes the results of the previous four steps, along with processing restrictions in the card and the chip, and sends a request to the chip for a decision to approve offline, decline offline, or go online for processing.
Card Action Analysis - Based on rules and limits set by the issuer the chip will respond with one of three choices
- ARQC: go online;
- AAC: offline decline
- TC: offline approval
Online Processing - If the decision is made to go online, then the terminal sends an online request to the issuer host for card authentication and authorization. If the response includes optional issuer authentication (ARPC), the terminal will send data to the chip for verification. (See “Online processing” below.)
Completion and script processing - Transaction is completed. If online processing occurred, the chip must respond with a TC (approval) or an AAC (decline), and apply any script commands from the issuer host.
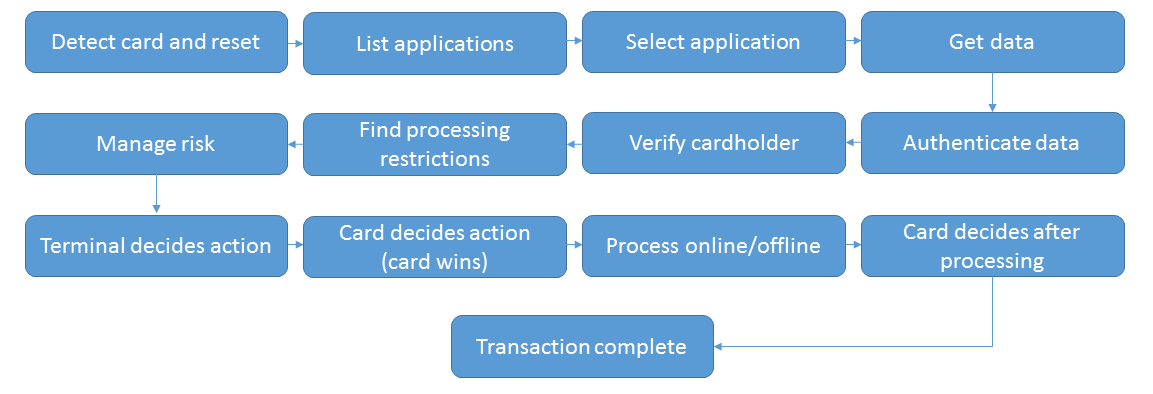
Example of the EMV transaction process
 Online processing
Online processing
For all communication involved in online and offline transactions, the EMV specifications define the message formats. If the transaction is to go online, the card application generates an ARQC (authorization request cryptogram), which the terminal includes in its authorization request to the network. The ARQC includes the transactions details, the card authentication method (CAM), and a cryptogram designed for one-time use. As the issuer receives the request, it generates its own cryptogram from the transaction data using the private 3-DES key, which is known only to the issuer and the chip. If this cryptogram matches the cryptogram sent by the terminal, the issuer knows the card is genuine, and not counterfeit. The issuer then responds with an ARPC (authorization response cryptogram), which either accepts or declines the transaction. The ARPC may also contain an issuer script (a new set of commands to be sent to the card). The ARPC can include another cryptogram, which the chip can use to verify the issuer.
Offline processing
SDA is used to authenticate the payment card itself, and verify that selected card information from the issuer hasn't changed since it has been issued.
SDA does not require cryptographic processing by the chip, since it uses a “static cryptogram” permanently stored on the chip. This cryptogram was previously generated by selected card information on the chip. The cryptogram must have been signed by the private key of the issuer’s RSA key pair.
During a payment transaction, the card sends this signed static cryptogram, the CA index, and the issuer certificate to the terminal.
Since SDA presents the same data in every transaction, this data can easily be used by attackers to create a clone. The static cryptogram and the digital certificate are static information, and hence are independent of the actual transaction.
An EMV chip using the Dynamic data authentication (DDA) method ensures protection against cloning attacks by creating a “dynamic cryptogram” that is unique to the transaction.
- offline PIN,
- online PIN,
- signature, or
- no CVM.
About the 3-DES cryptographic protocol
About the Certificate Authority (CA)
About the EMV card issuing process
Conclusion
Cryptomathic is a highly experienced EMV vendor assisting any type of organisation to move to chip, including banks, third party service providers and payment schemes.
• Data preparation
• Key management
• Certification authority
• Card management
• Compliance assurance, e.g. payment scheme and PCI DSS
References and further reading
- Selected articles on Key Management (2012-16) and EMV, by Ashiq JA, Chuck Easttom, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Matt Landrock, Peter Landrock, Steve Marshall, Torben Pedersen, Maria Stokes, John Trankenschuh and more
- Contact Chip Card Online Authentication (2014) by the EMV Migration Forum
- EMV Key Management – Explained (2015) by Cryptomathic
- EMV Migration Forum by the EMV Connection (retrieved: October 2015)
- A Guide to EMV (2011) by the EMVCo, LLC
- Chip-and-PIN vs. Chip-and-Signature (2012) by John Kiernan
- Cryptography of EMV cards (2014) by Yefim L. Leifman
- How secure is Chip and PIN? (2008) by Susan Watts
- EMV Payment Security – A Brief Overview (2014) by Dan Boneh
Image: "Credit cards on keyboard" courtesy of GotCredit, Flickr (CC BY 2.0)


