2 min read
The SolarWinds attack and best practices for code-signing
Since the announcement of the SolarWinds supply chain attack, intensive analysis has been done by Crowdstrike, FireEye (with additional details),...
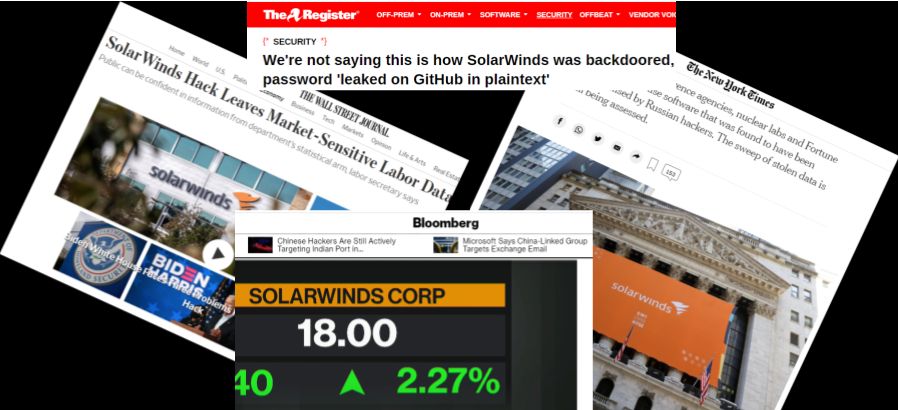
2 min read
Since the announcement of the SolarWinds supply chain attack, intensive analysis has been done by Crowdstrike, FireEye (with additional details),...

3 min read
The rise of quantum computing is expected to have significant impacts on both financial and technological considerations when evaluating...
4 min read
Tokenization is a generalized concept of a cryptographic hash. It means representing something by a symbol (‘token’).

3 min read
The first practical chosen-prefix collision attack on SHA-1 was announced in January 2020 by researchers Gaëtan Leurent and Thomas Peyrin: “SHA-1 is...

3 min read
This article discusses recent warnings that a chosen-prefix collision attack on SHA-1 is now practical and cost-effective for attackers.

5 min read
The EMV consortium released several standards detailing how “network” tokenization should be handled. There is now a general consensus within the...
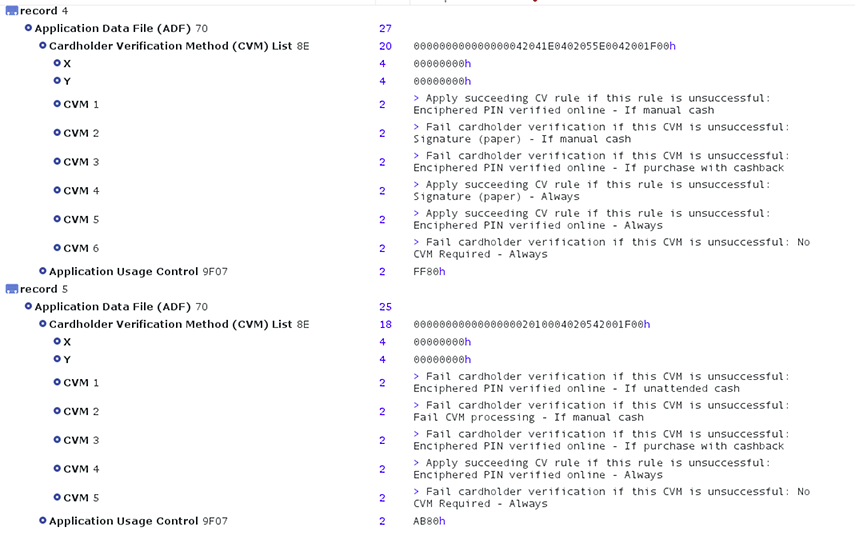
6 min read
EMV is short for EUROPAY-VISA-MASTERCARD. This term is used to refer to standards that have been designed to improve the security of credit and debit...

4 min read
The concept of a token has been used in the digital world for almost 50 years to separate and protect real data elements from exposure. In recent...

3 min read
Crypto-agility, or cryptographic agility, is the capacity for an information security system to adopt an alternative to the original encryption...