3 min read
Understanding non-repudiation of origin & non-repudiation of emission
Cryptomathic : 20. October 2016

- Home >
- Understanding non-repudiation of origin & non-repudiation of emission
This article sheds light on the two approaches to achieve non-repudiation of an electronic message: non-repudiation of emission and non-repudiation of origin.
Non-repudiation is the assurance that someone cannot successfully deny the validity of something. Typically, non-repudiation refers to the ability to ensure that a party to a contract or a communication cannot refuse the authenticity of their signature on a document or that a message was actually sent.
Role of the Digital Signature
In the cyber space, an important mechanism to achieve non-repudiation is a digital signature. In Europe, eIDAS provides standards for using advanced electronic signatures or qualified electronic signatures for when a higher level of assurance is required.
An advanced electronic signature must:
- Be uniquely linked to the signatory
- Identify the signatory
- Be created through means, which the signatory keeps under his or her sole control
- Have been linked to the data in which it relates, and able to detect any change to said data
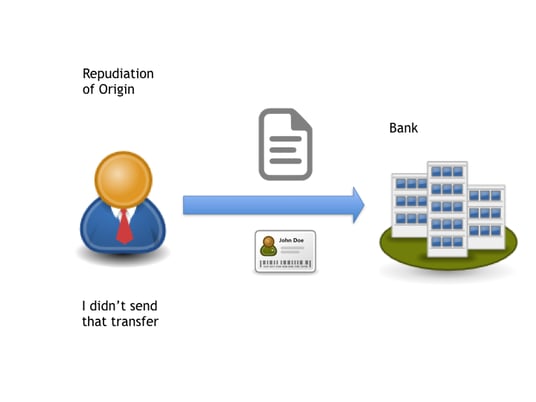
Non-Repudiation of Origin (NRO)
Non-repudiation of origin occurs at the application level for U2A messages, which addresses the user denying they have sent a message or either entity not recognizing the message content. With NRO, the technical solution remains visible for users to enter additional input via pop-up screens when required. For example, NRO can be assured through three solutions for U2A messages:
- Technical NRO, where a request to enter a authentication code will appear in a pop up after each input screen. Strong authentication of the user proves that the user has sent the message because the application authenticates the signature that has been digitally produced.
- Technical NRO for Critical Screens, which works similar to Technical NRO, but the pop up request for authentication only occurs on critical screens which update cash or securities balances. Non-critical screens are not projected.
- Legal NRO is the equivalent of NRE + Clause in FA, where the clause is equivalent to European “log file.” The message is signed with the user’s digital certificate, providing evidence that the message originated from the user.
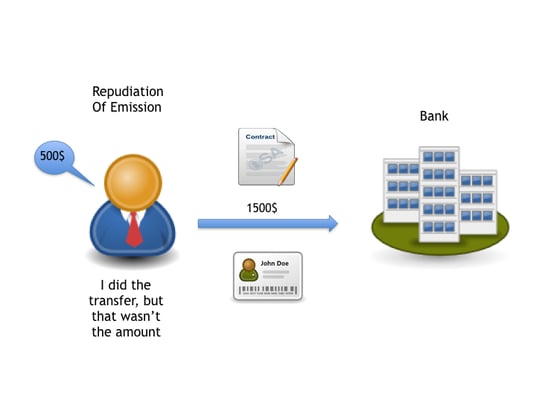
Non-Repudiation of Emission (NRE)
Non-repudiation of emission occurs at the network level for user-to-application (U2A) messages. NRE makes a link between the sender of the message and the specific content of the message. It can provide legal evidence that a person sent that particular message. NRE is accomplished through a signature created at the network level. This is unseen from the user’s point of view. The NRE process includes:
- Encryption of data before being sent through the network
- The digital signature added proves that the message has been initiated by the client/user.
Legal Implications of Non-Repudiation
In the event of litigation, the trust service provider must be able to provide sufficient evidence that the signature process was carried out by the user. This is usually done by providing the entire audit trail for the said operation, which may also be complemented when the certified signature service provides a well-defined liability shift.
To remove doubts of repudiation, three technical challenges must also be met:
- Assuring that the signature key has been bound to the identifiable person or organization
- Guaranteeing that the end user maintains sole control over his or her private key that has been used for signature operations
- Inclusion of a strong experience of What You See Is What You Sign(WYSIWYS) in the signing process
The legal value provided by an advanced electronic signature is important. It works to ensure that the integrity of the message or document has not been altered during transit. The message or data will be deemed complete by the court as it has not been altered and its integrity cannot be denied.
How to Demonstrate Non-Repudiation
Non repudiation demonstration can be technically accomplished, when the operator / verifier of a transaction (e.g., a bank) is able to provide an extensive audit trail for an operation, giving suitable evidence that:
- A given transaction existed at a given point in time. A hash of such data was generated before the signature process has actually started.
- The said transaction is rendered in an non-altered way to the end-user, using a trusted viewer, where the content is passed to the user through a second channel.
- Log entries are created on the server side when the data is visualised.
- There is a proof of user presence and that the user has sole control of their signing key through 2FA, substantiated through the logs.
- There is a signature of the data to be signed and there are secure logs generated by the digital signature creation process, thereby guarantying data integrity and proof of intent of the user committing to the data with his signature.
References and Further Reading
- Selected articles on Authentication (2014-16), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard and Dawn M. Turner
- Selected articles on Electronic Signing and Digital Signatures (2014-16), by Ashiq JA, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner and Tricia Wittig
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
- Recommendations for the Security of Internet Payments (Final Version) (2013), by the European Central Bank
- Draft NIST Special Publication 800-63-3: Digital Authentication Guideline (2016), by the National Institute of Standards and Technology, USA.
- NIST Special Publication 800-63-2: Electronic Authentication Guideline (2013), by the National Institute of Standards and Technology, USA.
- Security Controls Related to Internat Banking Services (2016), Hong Kong Monetary Authority
Image: Isometric Spotlight, courtesy of Aidan Gibbons, Flickr (CC BY 2.0)