3 min read
EBA on PSD2 Customer Authentication: Possession & Knowledge
Cryptomathic : modified on 24. September 2019

- Home >
- EBA on PSD2 Customer Authentication: Possession & Knowledge
Financial institutions and solution providers are busy implementing the requirements of Strong Customer Authentication (SCA) under the Revised Payment Services Directive (PSD2) and the Regulatory Technical Standards (RTS).
However, as with any new regulatory directive, there has been a certain amount of ambiguity as to what elements comply fully with the SCA constraints and what elements fall short. To remedy this, the European Banking Authority has been issuing its opinions on the technical requirements related to eIDAS, SCA and so on.
The latest such opinion was published in June 2019 which provides valuable insights into what elements the EBA considers to be compliant with SCA requirements. In Part 1 of our series, we analysed EBA’s opinion on the elements under the category of inherence. Today, we look at possession and knowledge.
Possession
PSD2 defines possession as “something only the user possesses”. Possession does not need to be physical but may also be digital. The essential condition is that unauthorised access or replication of that element must be prevented with adequate safeguards.
Devices can be used as proof of possession as per the EBA provided that there exists a “reliable means to confirm possession through the generation or receipt of a dynamic validation element on the device”. An example of this are the one-time passwords (OTP) that are received as SMS’s or through push notifications etc. An app or browser than can ensure a unique connection with a user’s device is also a compliant possession element. This may be done through hardware crypto-security, device registration or other such means. Other examples of valid possession elements include digital signatures or quick response codes that may be scanned by a device.
The accompanying table lists some of the observations made by the EBA in this regard.

Source: European Banking Authority
Knowledge
PSD2 defines knowledge as “something only the user knows”. It’s not surprising, therefore, that the main requirement for this element under SCA is that it must not be uncovered by or disclosed to unauthorised parties. This includes the more traditional elements like passwords, PINs, swipe patterns, responses to challenge questions and so on. Non secret details like user IDs or email addresses do not qualify though.
This category is actually pretty straightforward although the treatment of cards and their attributes is interesting. Card details and the security code shall not be a valid knowledge element as per the EBA. Some cards now come with dynamic security codes and those may be considered valid possession elements but not valid knowledge elements. However, if the card security code is not printed on the card and was sent separately to the user, it shall be a valid knowledge element as it not much different from a PIN in that sense.
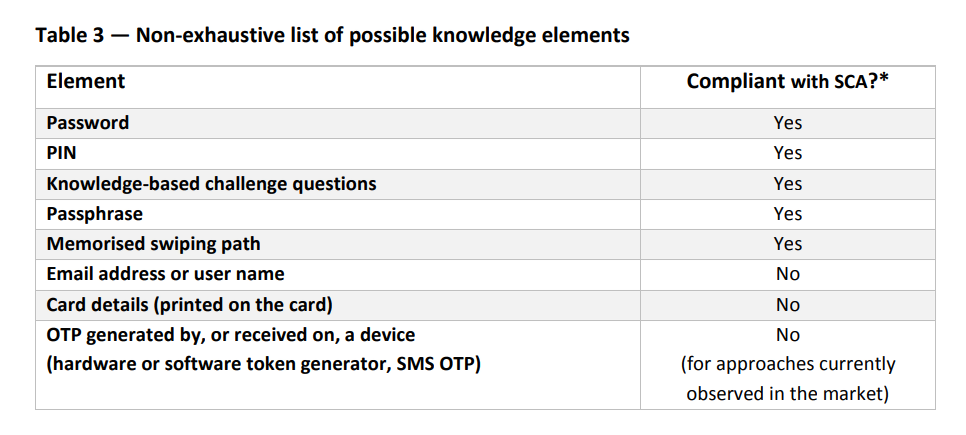
Source: European Banking Authority
The big picture
SCA requires at least two elements from any two of these three categories at a minimum. However, it is crucial for those elements to be independent to each other. Which means that breach of one element, cannot possibly compromise the other. Lastly, remote transactions also require dynamic linking so that any elements generated for one transaction cannot be used for another.

References and Further Reading
- EBA publishes an Opinion on the elements of strong customer authentication under PSD2 (June 2019), by the European Banking Authority
- EBA publishes an Opinion on the use of eIDAS certificates under PSD2 (December 2018), by the European Banking Authority
- The new ETSI standard for eIDAS qualified certificates supporting the PSD2 directive (December 2018), by Michal Tabor
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- Selected articles on Authentication (2014-today), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner and more
- eIDAS webinar 1: Using electronic Identification, Authentication and trust Services for Business (2018), by the European Commission
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission
- Proposal for a DIRECTIVE OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL amending Directive (EU) 2015/849 on the prevention of the use of the financial system for the purposes of money laundering or terrorist financing (2016), by the European Commission
- REGULATION (EU) 2016/679 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (2016), by the European Parliament and the European Council
-
Proposal for a REGULATION concerning the respect for private life and the protection of personal data in electronic communications and repealing Directive 2002/58/EC (Regulation on Privacy and Electronic Communications), (2017), by the European Parliament and the European Council
- Revised Directive 2015/2366 on Payment Services (commonly known as PSD2) (2015), by the European Parliament and the Council of the European Union
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
-
DIRECTIVE 2013/37/EU amending Directive 2003/98/EC on the re-use of public sector information (2013) by the European Parliament and the Council